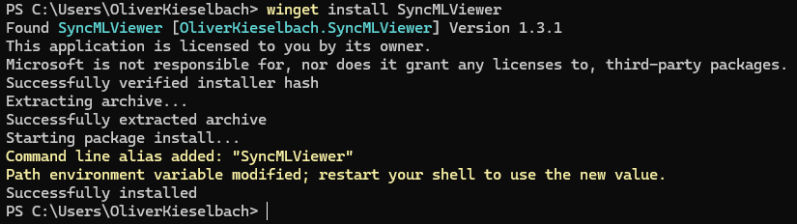
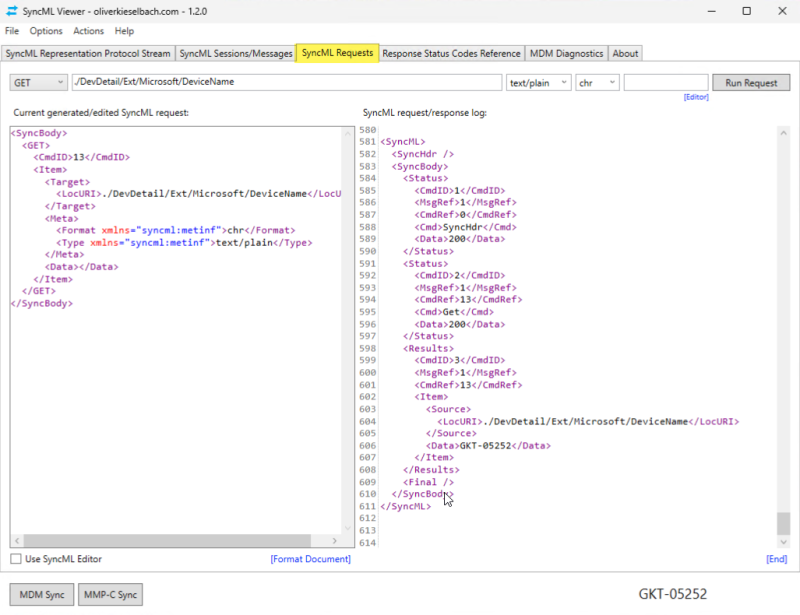
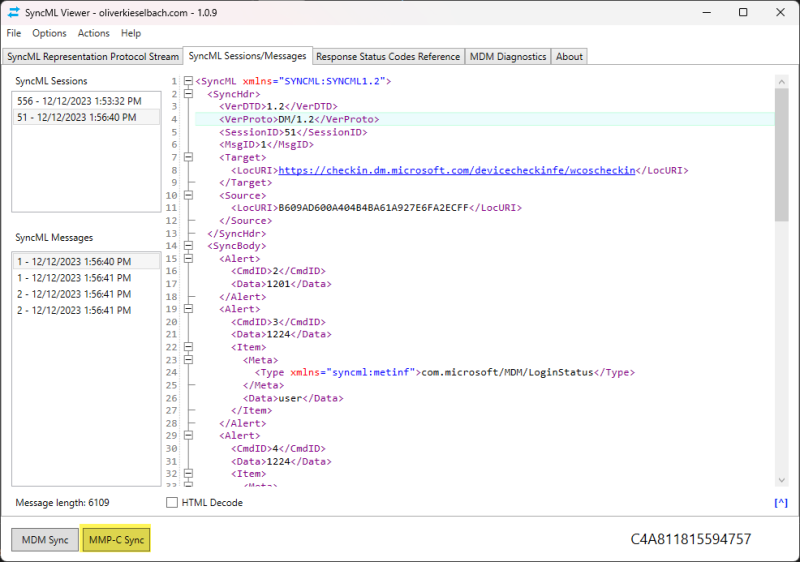
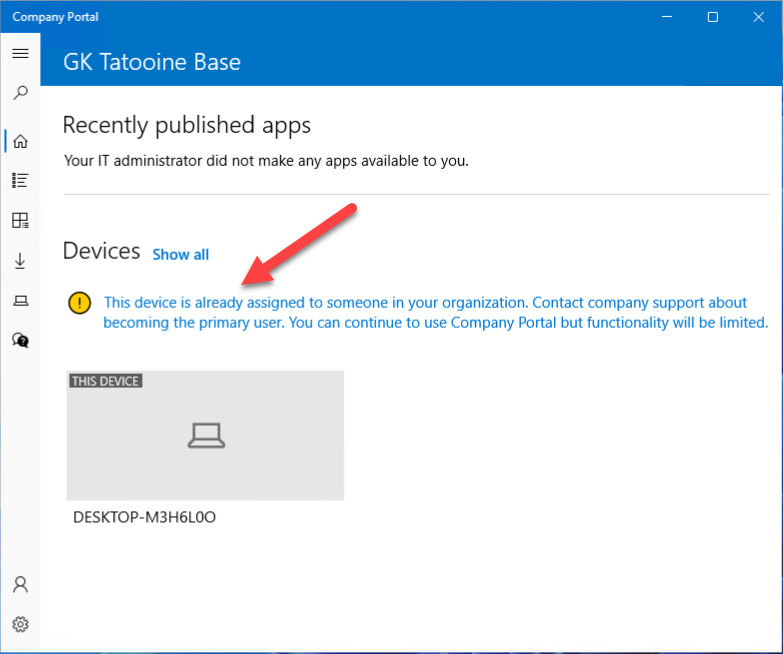
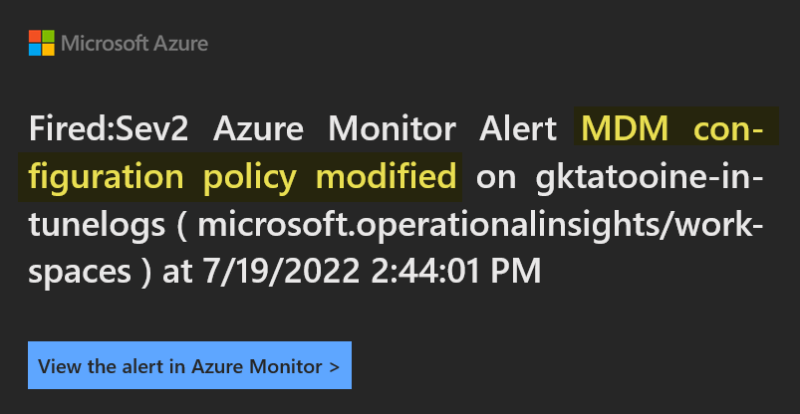
To make your life easier, I’ve submitted SyncML Viewer to the official Windows Package Manager Community Repository (winget). From now on you can get it by a simple command: winget install SyncMLViewer After a quick install you can use it: You have to open a new shell as the path variable is updated, then type…
Read More