
In this guide I will have a look at an easy way to deploy device certificates to modern cloud managed clients. Even without an Microsoft on-premises PKI your devices will get device certificates. These certificates can be used for Wi-Fi authentication for example.
Normally if you want to deploy certificates to mobile devices you are looking at the Simple Certificate Enrollment Protocol (SCEP). To configure this you need to follow this guide Configure and use SCEP certificates with Intune which is fairly long and even takes about 30 min. to read. It involves various on-premises components like AD, CA, NDES Server, Microsoft Intune Certificate Connector and an Azure AD Application Proxy or WAP. A typical setup would look like this:
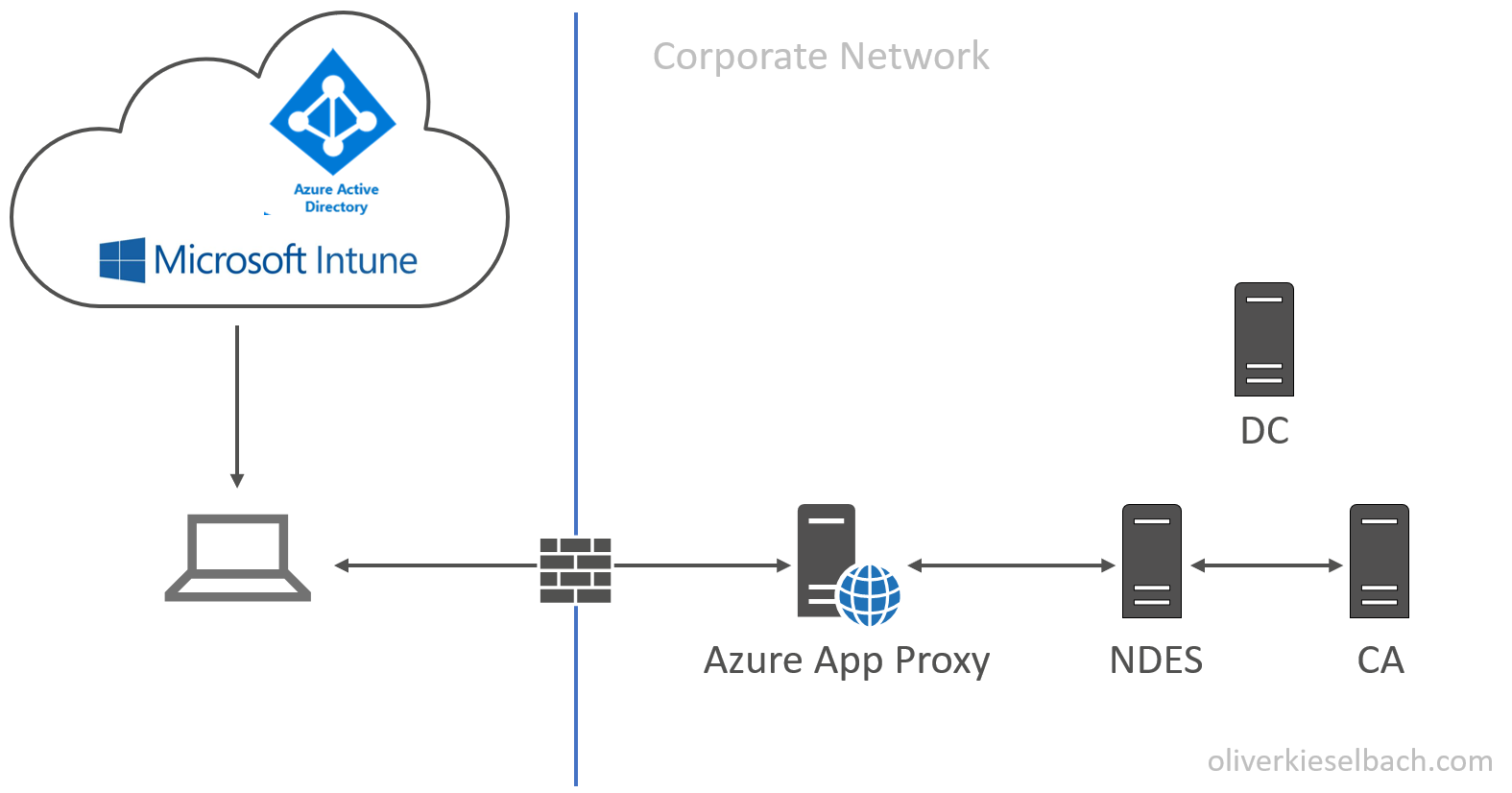
You might have most of the components in your infrastructure but often I see customers without all of these or they want to get rid of the technical PKI which is used for just a few workloads like 802.1x certificates and move on to a cloud infrastructure.
How do we achieve device certificate deployment the easy way?

There is a solution called SCEPman | Intune SCEP-as-a-Service build by Glück & Kanja Consulting AG available in the Azure Marketplace. All it needs is an active Azure Subscription.
A little background from the product description:
Microsoft Intune allows third-party certificate authorities (CA) to issue and validate certificates using the Simple Certificate Enrollment Protocol (SCEP). SCEPman is a fully unattended Certificate Authority using Azure Key Vault for Microsoft Intune based device certificate deployment. (UPDATE: with SCEPman 1.3 user certificates are supported in a limited fashion) SCEPman is a .net core C# based Azure Web App providing the SCEP and Intune API. It uses an Azure Key Vault based Root CA and certificate signing. No other component is involved, neither a database nor any other stateful storage except the Azure Key Vault. That said, SCEPman will not need any backup procedures.
SCEPman is an Azure Web App with the following features:
- A SCEP interface that is compatible with the Intune SCEP open-source API in particular
- SCEPman signs machine authentication certificates with a CA key stored in Azure Key Vault
- SCEPman contains an OCSP responder to provide certificate validity in real-time. A certificate is valid if its corresponding AAD device exists and is enabled
A simple post request to SCEPman service creates the CA certificate.
However, if for whatever reason an alternative CA key material shall be used it is possible to replace this CA key and certificate with your own in Azure Key Vault. For example, if you want to use a Sub CA certificate signed by an existing internal Root CA.
SCEPman issues authentication certificates that are compatible with Intune’s internally used authentication certificates. They contain Intune’s extensions determining the tenant and the machine. Additionally, the tenant ID and machine ID is stored in the certificate subject to allow common Radius servers like Cisco ISE, FreeRADIUS, RADIUS-as-a-Service and others to use these certificates for authentication.
! Please read carefully – Warning about user certificates
SCEPman is intended to use for authentication and transport encryption certificates. That said, you can deploy user and device certificates used for network authentication, WiFi, VPN, RADIUS and similar services. Do not use SCEPman for email-encyrption or digital signatures (without a separate technology for key management). The nature of the SCEP protocol does not include a mechanism to backup or archive private key material. If you would use SCEP for email-encryption or digital signatures you may loose the keys to decrypt or verify at a later time.
How does the exact workflow look like?
As we already know it is a cloud service and uses an Azure Web App. Let’s look at the detailed certificate request workflow:
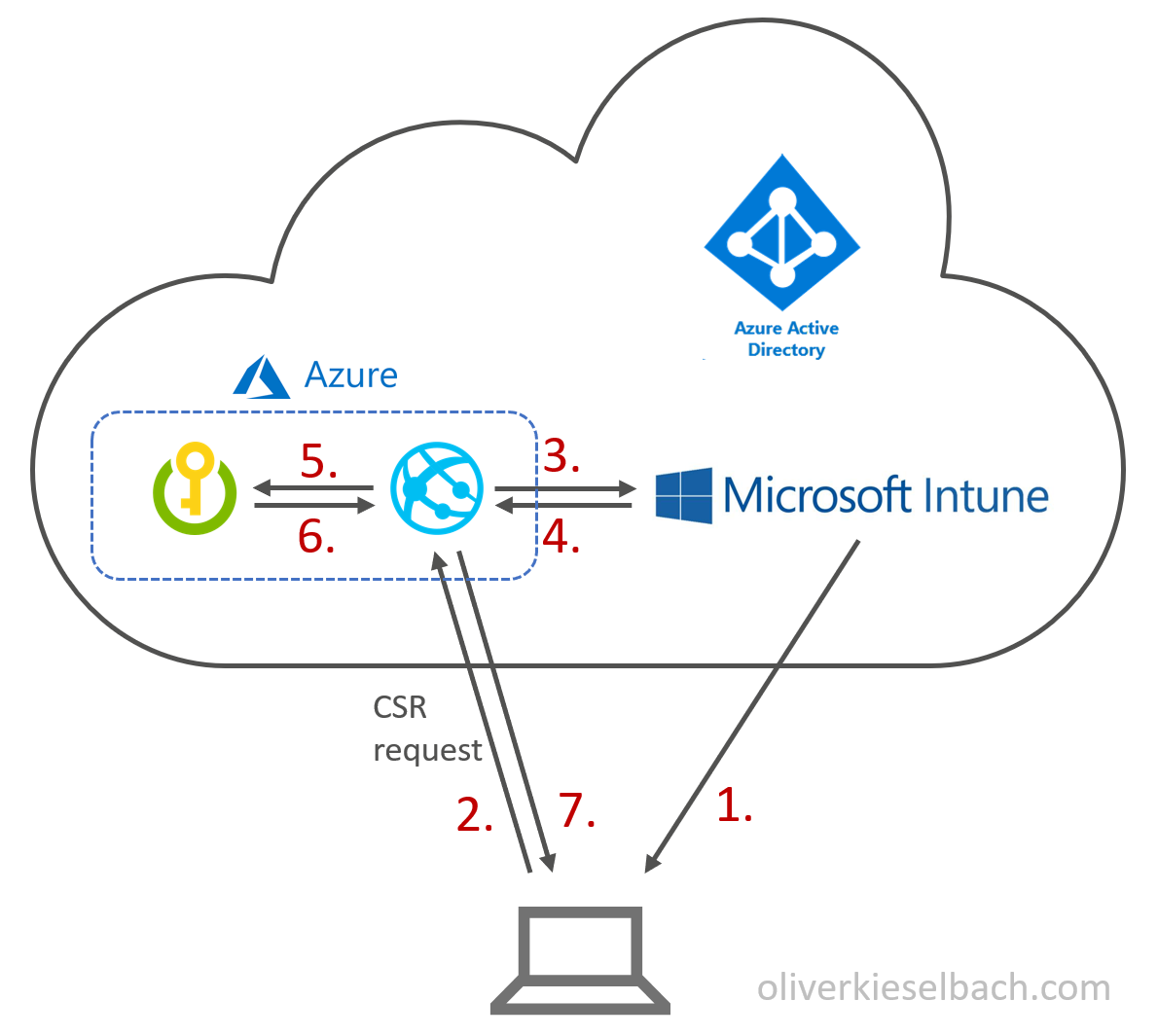
- In Intune you create and assign a new SCEP certificate profile and target it to a user or device group.
- The device (Windows, iOS, Android, macOS) checks in and requests a certificate from SCEPman (the Azure Web App)
- SCEPman requests validation of the request from Intune by comparing a unique challenge (this prevents tampering)
- Intune validates the CSR and sends back a response
- If the challenge is verified successfully, SCEPman will request certificate signing from the Azure Key Vault
- SCEPman will receive the signed certificate
- SCEPman will issue the certificate to the device
A more detailed technical certificate workflow can be found here Add partner certification authority in Intune using SCEP
SCEPman will act as an OCSP responder and the detailed workflow looks like this:
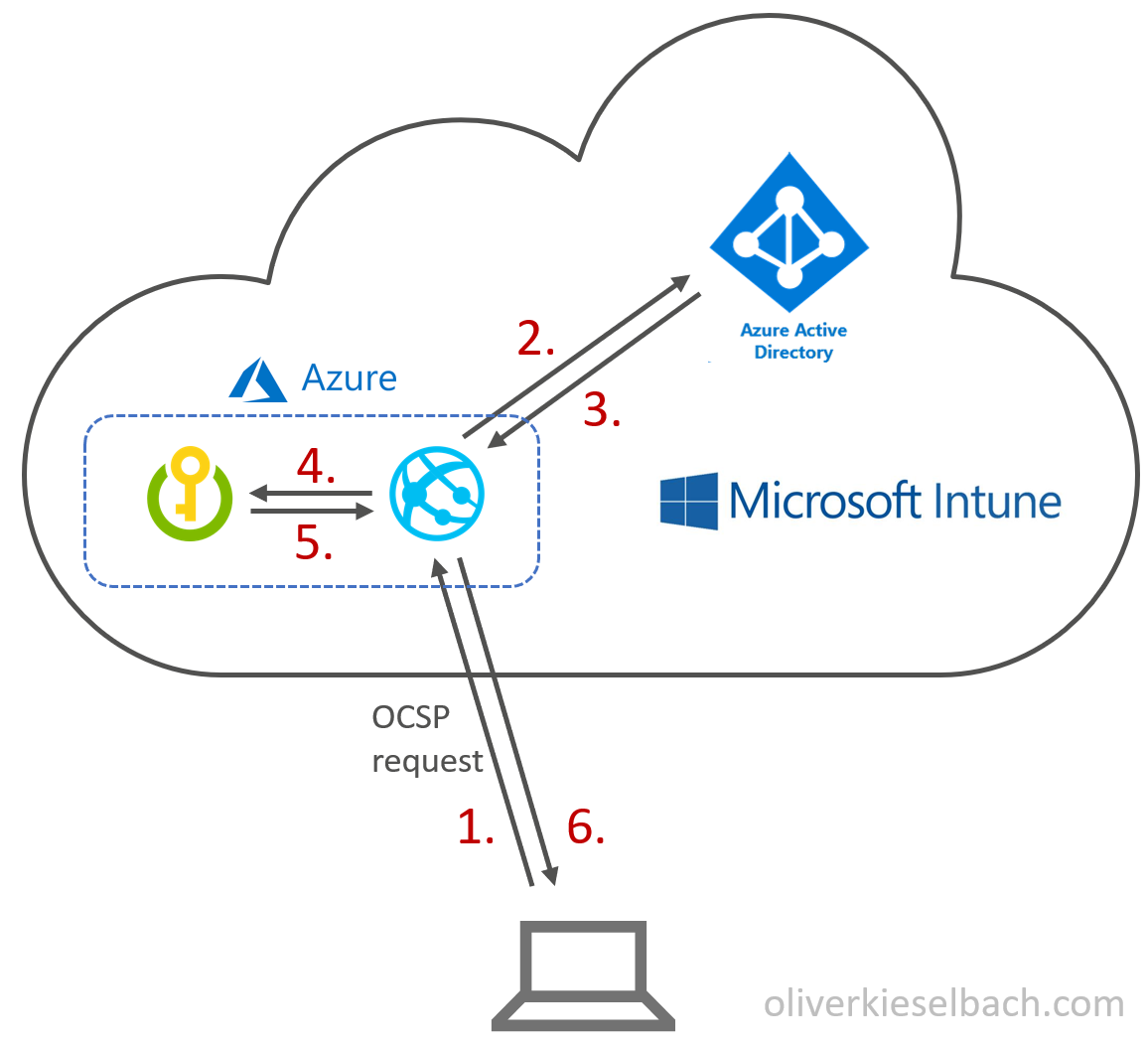
- The device sends an OCSP request for the certificate to SCEPman
- SCEPman checks if the device exists in Azure AD and is enabled
- SCEPman receives the results and if the AAD device is not available or disabled the OCSP response for the certificate is send as “not valid”
- For existing and enabled AAD devices SCEPman will verify the certificate with the Azure Key Vault
- The result is send back to SCEPman
- On successful verification it will send an OCSP response as “valid”, otherwise as “not valid”
How to deploy SCEPman now?
16.06.2021 Attention(!) there might be an issue with the App registration due to an introduced change to some tenants. In case your SCEPman instance does not deliver certificates since a few days. Have a look at this support article:
https://glueckkanja.zendesk.com/hc/en-us/articles/4402360224530-SCEPman-does-not-issue-certificates
Step 1: Azure AD App registration
First, we need some preparations upfront to allow SCEPman to talk to the Azure AD. This is achieved by registering an App for SCEPman in Azure AD.
- Login to your Azure Portal with an Admin Account
- Navigate to Azure Active Directory
- Choose App registrations
- Click New registration
- Set display name to SCEPman
- Set supported account types to Accounts in this organizational directory only
- Click Register
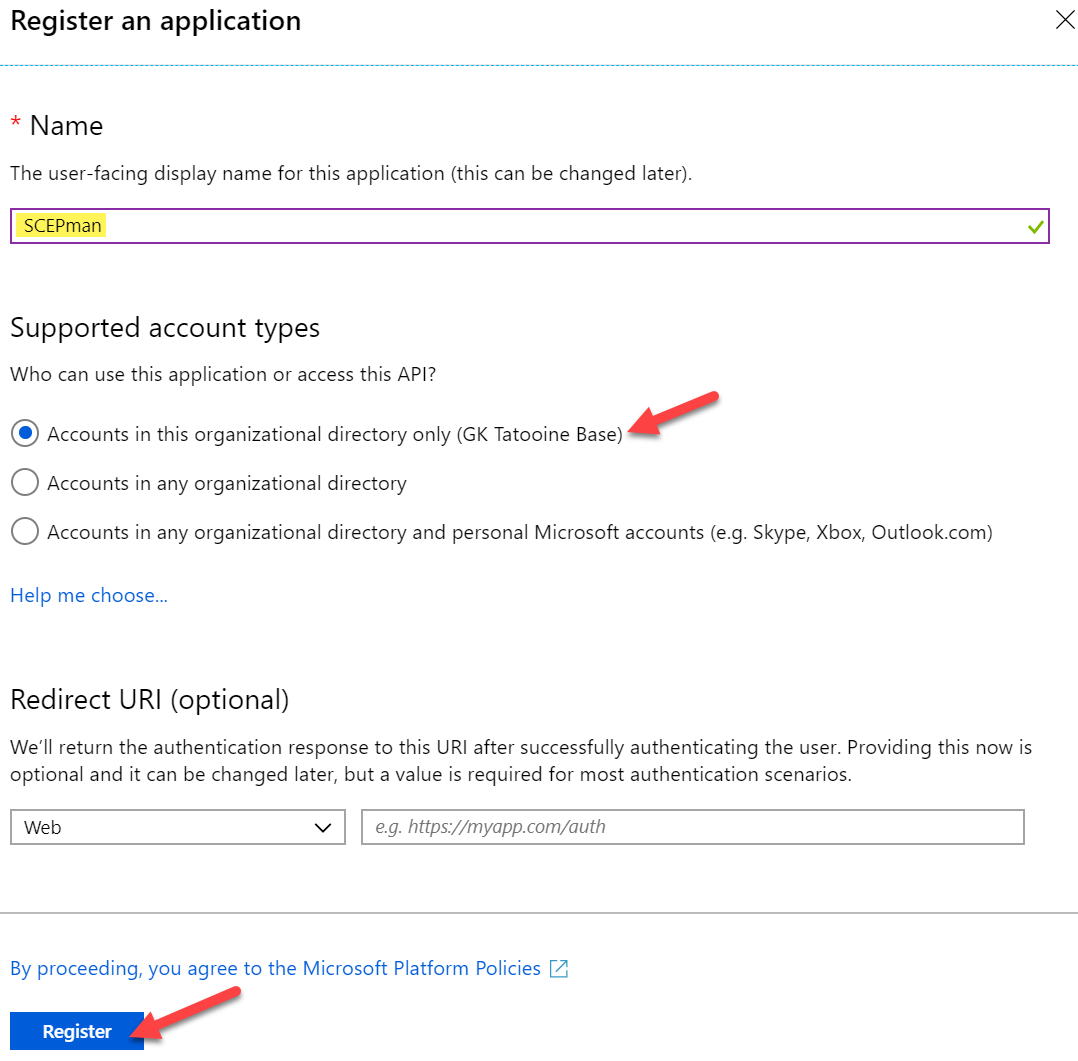
Next we need to copy and save the created Application (client) ID for the newly registered app SCEPman somewhere (e.g. notepad):

Now we need to create a client secret
- Select the Certificates & secrets blade
- Add a new client secret with New client secret
- Define a Description and set expiration to
Never24 months (configuring never is not possible anymore, so create immediately a recurring calendar entry to refresh the secret after ~1,5 year) - Save the generated secret somewhere because you are not able to look it up again

The registered Azure AD app SCEPman now needs to have API permissions which we will grant now:
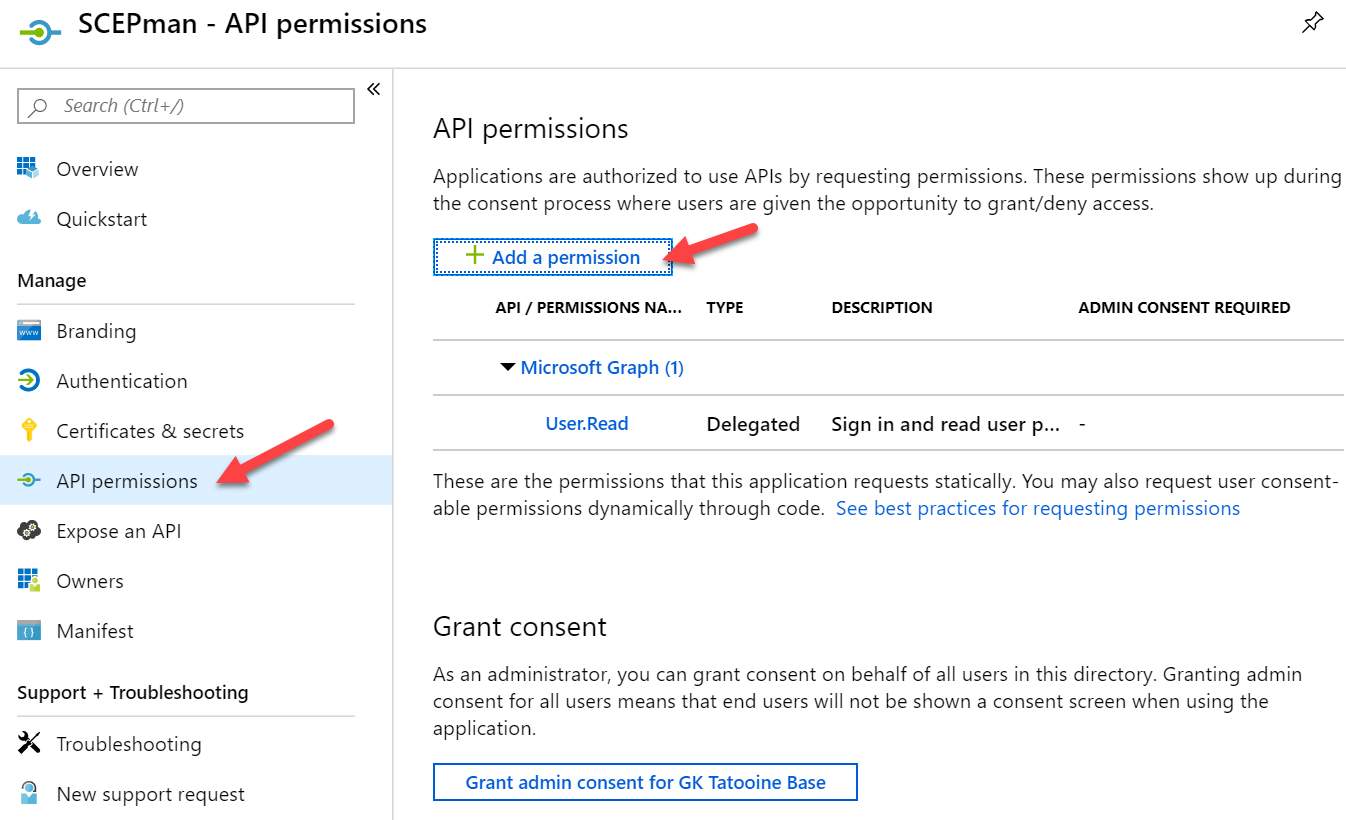
- Select the API permissions blade
- Click Add a permission to grant required permissions
- Select Intune
- Choose Application permissions as the permission type
- Click scep_challenge_provider and confirm with Add permission

- Click Add a permission once again
- Now select Microsoft Graph
- Choose Application permissions as the permission type
- Expand Directory and check Directory.Read.All and confirm with Add permission
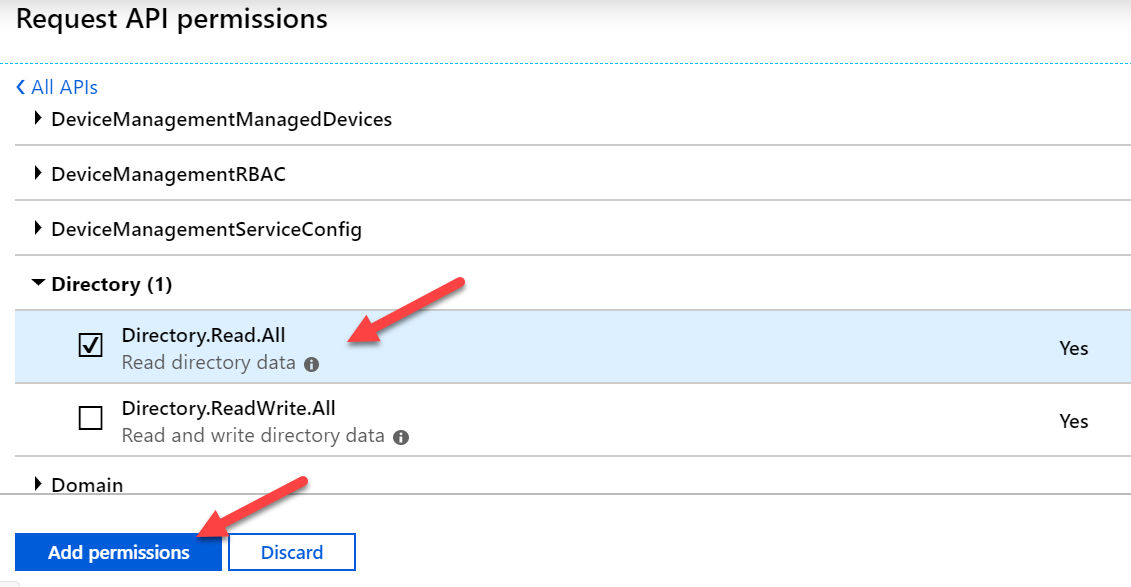
And really important as some tenants have already issues and on January 2022 you will need to have the additional API permission Application.Read.All for Azure Active Directory Graph. Please read carefully, not Microsoft Graph the API needed API permission is for the old graph API called Azure Active Directory Graph. This is how it must look like in the end:

- Click Add a permission once again
- Now select Azure Active Directory Graph
- Choose Application permissions as the permission type
- Expand Directory and check Application.Read.All and confirm with Add permission

Finally Click Grant admin consent for <your tenant name> and confirm the displayed dialog with Yes


The Azure AD app registration is finished now.
Step 2: SCEPman Deployment – Azure Marketplace
As already said SCEPman is an Azure Marketplace solution and can be easily deployed from there. Just search for SCEP and use the link for SCEPman:
Click on the Create button
Follow the Wizard and fill in the required fields for section Basics:

Fill in the Azure AD app registration details for SCEPman (copied earlier):
Wait for validation passed and click OK
Click on Create and wait for the deployment

Check if SCEPman is running by navigating to Azure AD > App services > scepman-<a-random-string> and click on Browse to see the SCEPman website:
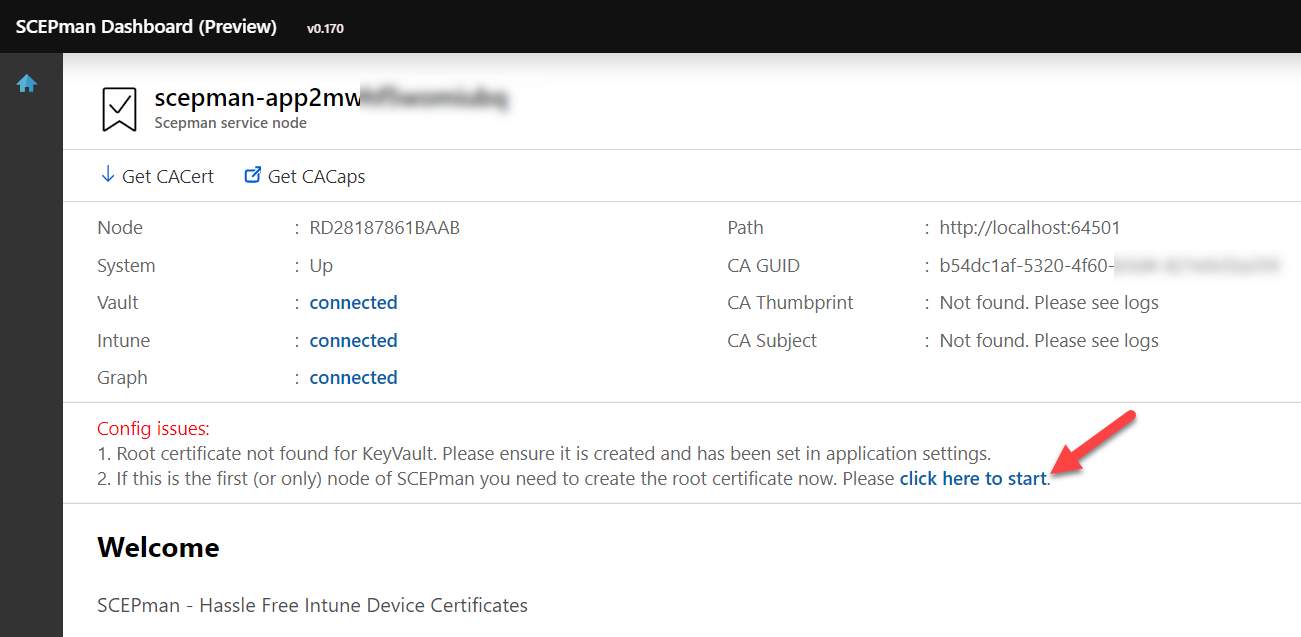
If everything went well you should see the Vault, Intune and Graph as connected. As this is our first and single node in this deployment we can click on “click here to start” to create the Azure Key Vault RootCA certificate (this takes one or two minutes):

Remember this can also be changed to a custom RootCA certificate (not described in this guide). If there is no need, you can create the new RootCA certificate now (SCEPman-Device-Root-CA-V1). If you plan to use the certificates for Wi-Fi authentication, your RADIUS must trust the public root certificate. The public root certificate can be easily downloaded from the SCEPman website by clicking on Get CACert:

To get continuous updates for SCEPman you can point a configuration variable to the maintained GitHub repository of SCEPman. During every restart the Azure Web App will do a check and a copy deployment if necessary. To configure this, go to SCEPman in Azure AD > App services > scepman-<a-random-string> and click on Configuration:

Look for WEBSITE_RUN_FROM_PACKAGE and replace the URL with the SCEPman GitHub URL:
https://raw.githubusercontent.com/glueckkanja/gk-scepman/master/dist/Artifacts.zip
Step 3: Deploying device certificates via Intune Certificate profile
First, we need to trust the public root certificate from SCEPman. Therefore, we download the CA certificate (shown above) and deploy it via a trusted certificate profile in Microsoft Intune:

When finished we can deploy this to our devices.
Second, we need to create a SCEP certificate profile to deploy the device certificates. To fill the properties of the SCEP certificate profile we need the SCEP Server URL. The base SCEP Server URL can be found on the Overview of the App Service of SCEPman:

To complete the URL, append /certsrv/mscep/mscep.dll (compare SCEP certificate profile picture above). The final URL should look similar like this (xxx is a random string), copy this URL to a notepad for example:
https://scepman-xxx.azurewebsites.net/certsrv/mscep/mscep.dll
Now we create a SCEP certificate profile in Intune to finally deploy the device certificates:

You should have two configuration profiles now:

Assign them to the same AAD user or device group to make sure the user or device overlaps and both profiles are targeted to the device. Don’t mix user and device groups. If you see pending as status for the configurations profiles in Intune for a long time, the assignment is probably wrong!
Verify device certificate deployment on a mobile client
Once we configured Windows configuration profiles, we verify successful deployment on an Azure AD joined Windows 10 device. Of course, you can create iOS, macOS, and Android profiles as well. All platforms are supported by the SCEP Server – SCEPman. Let’s verify if a client received successfully the trusted root certificate and the device certificate:
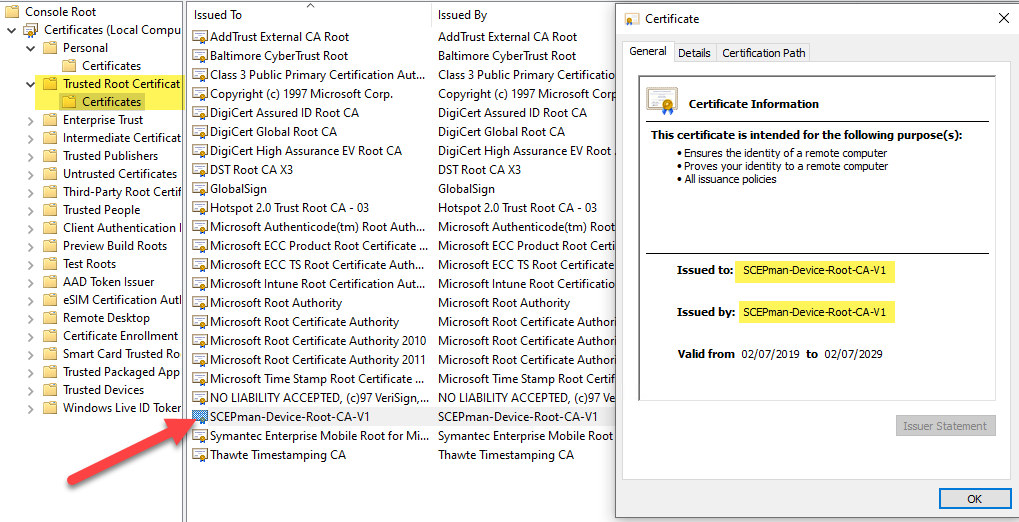

As you can see the device certificate is issued to a GUID and this GUID is the device ID of the Azure AD device object. Same principle and properties like Microsoft is deploying the MS-Organization-Access certificate to the device:

Additionally to show the iOS compatibility I created and deployed two policies for iOS (trusted root and SCEP profile). Here is a screenshot of a successful deployment via SCEPman on an iOS device:
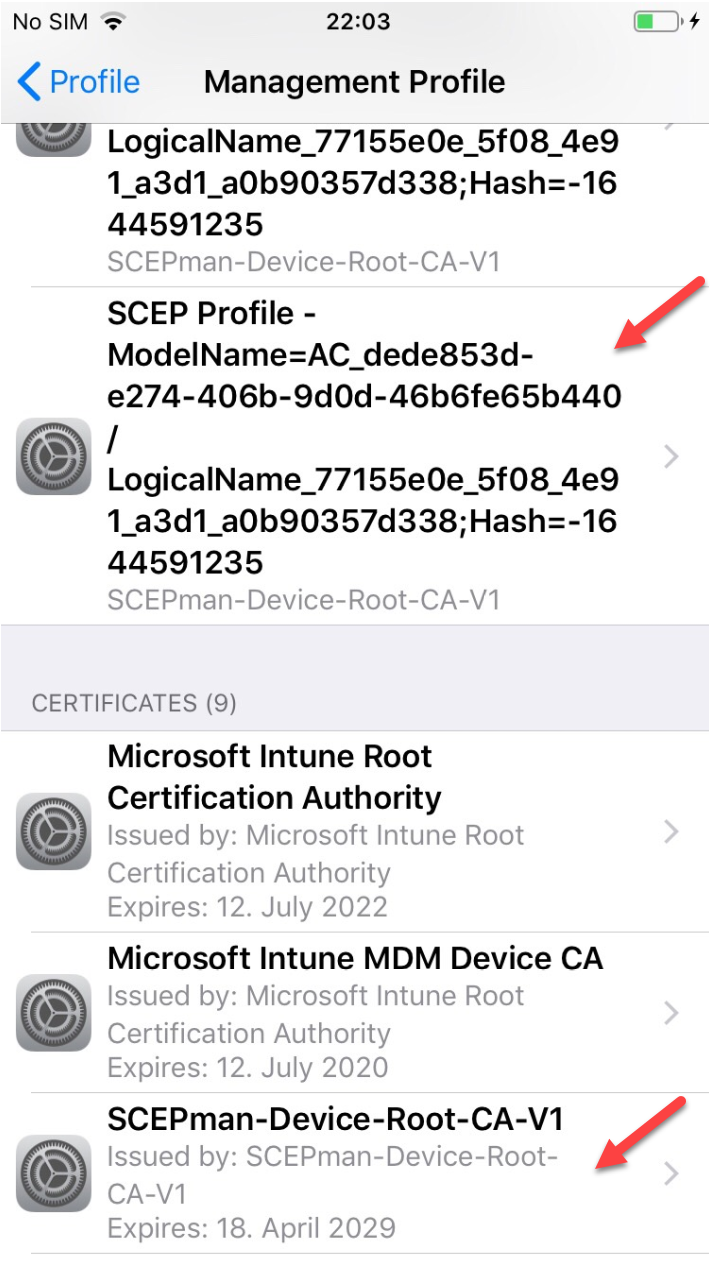
If you want to deploy Android Enterprise Work Profile and SCEP profiles for certificate usage with Wi-Fi, you should use the SAN attributes UPN in the SCEP profile otherwise Android will not find successfully the certificate for Wi-Fi usage. It is important to use the domain part of your logon user of the Company Portal:
Tip: To check if the certificate is successful deployed and available in the Android Enterprise Work profile you have to download the “My Certificates” app from the Google Play store within the work profile, otherwise you will not see the certificate.
What about revocation of a device certificate?
First, we need to check the validity of the device certificate. Therefore, open a command prompt as Administrator and type the following command:
certutil -verifyStore MY
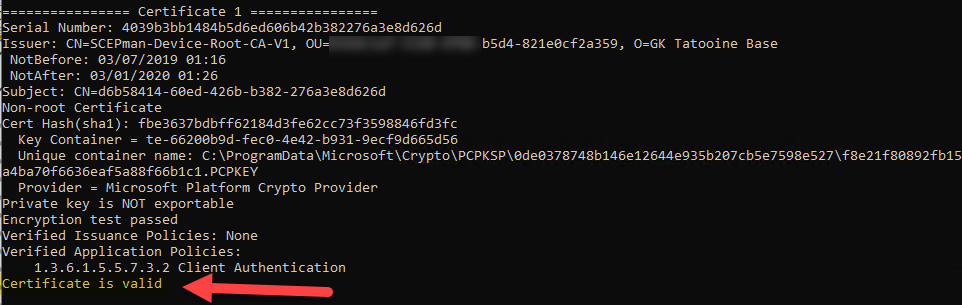
Look at the certificate with the device id issued by the SCEPman-Device-Root-CA-V1 and verify if the certificate is valid (see last line).
To verify that the OCSP responder is working, we can look at the OCSP url cache with the following command:
certutil -urlcache OCSP

Now if we want to revoke a device certificate, we have two options: deleting the device from Azure AD or just disabling it. I’m disabling it and verify again to see if the certificate will be revoked:
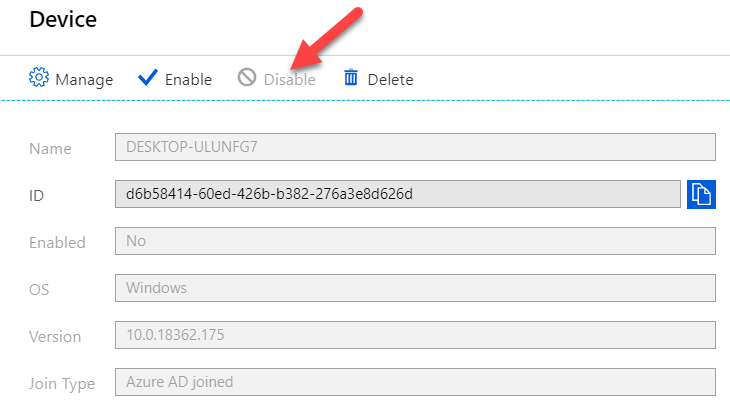

Now type again the following command:
certutil -verifyStore MY

If we enable the device in Azure AD again the device certificate should be marked as valid again. This can take up to 5 min.
An alternative method is to export the device certificate and use certutil to display a small certutil UI for the OSCP check:
certutil -url <path-to-exported-device-certificate>

Troubleshooting
Following a few steps for troubleshooting I used during evaluation. I really recommend to have a look at the official SCEPman Docs as well, as everything about SCEPman is documented there (design, architecture and so on) and also a good troubleshooting section. See SCEPman Docs
My trusted root certificate is deployed but my device certificate via SCEP profile results in an error?
The SCEP profile will result in an error if the certificate deployment wasn’t successful. This can have several reasons:
- SCEP certificate profile is configured with an error. For example, a wrong trusted root certificate was selected in the SCEP certificate profile. This is also shown in the event log under Events > Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin, EventID 32, SCEP: Certificate enroll failed. Result: (hash value is not correct.).

- SCEPman Azure Web App is not running. Check if the Azure resource is up and running.
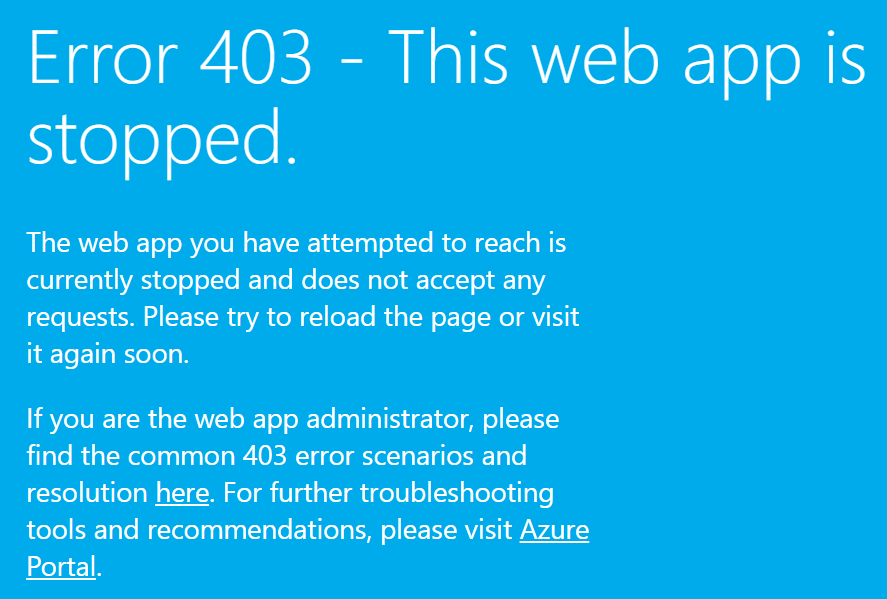
- SCEPman has a configuration or internal problem. Check Azure Web App log files via Advanced Tools > Kudu > Debug Console > CMD > navigate to LogFiles > Application > click on the download icon on the latest .txt file and review it
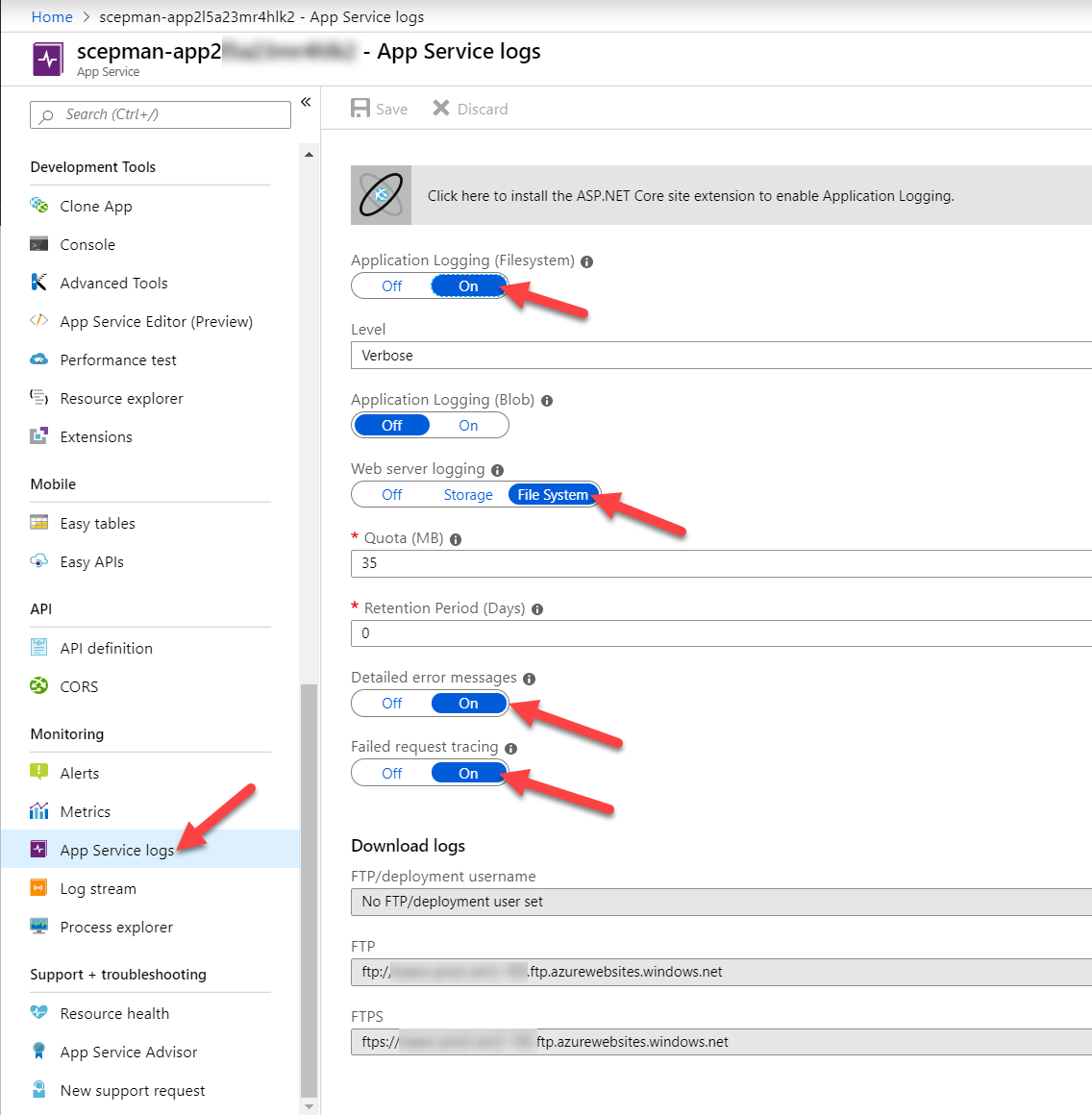
- Additional way of logging, configure the App Services Logs and check the Log Stream of the App Service. This might be a good way to troubleshoot 500 errors:
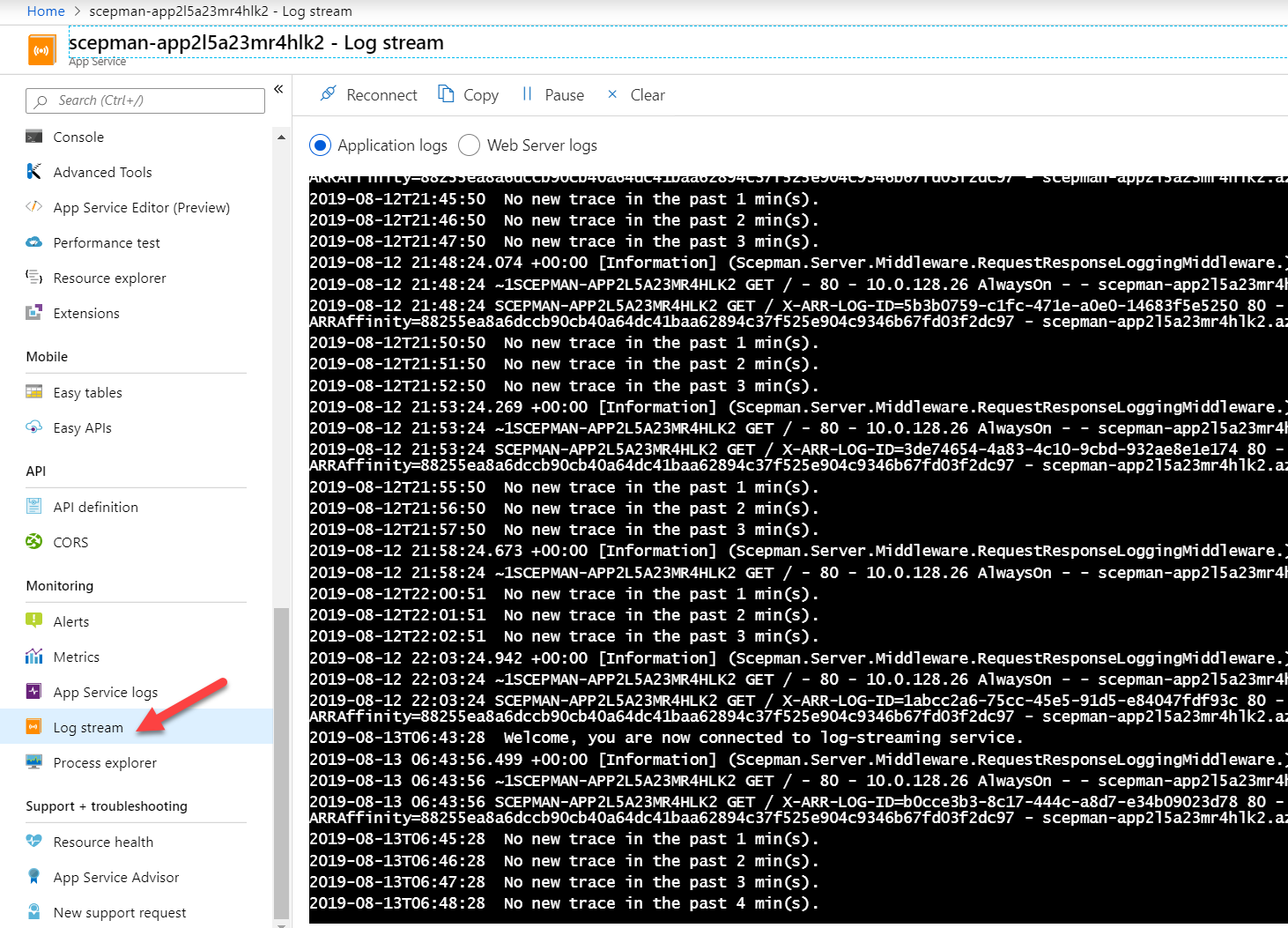
My certificate does not have the correct OCSP URL entry?
If the device certificate has a localhost URL for the OCSP entry in the certificate like this:
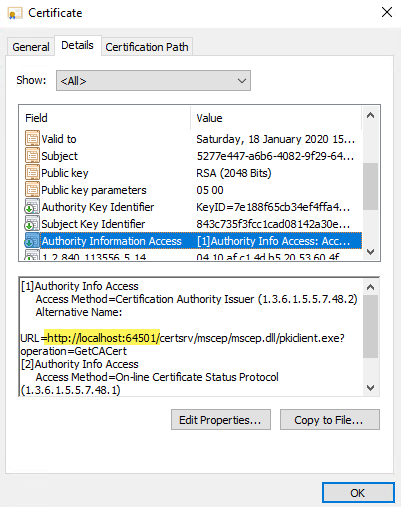
The App Service is missing an important Application setting with the name AppConfig:BaseUrl set to the azurewebsite URL. To fix this add the variable and save the App Service config:
AppConfig:BaseUrl https://scepman-XXXXX.azurewebsites.net
Delete the certificate from the device and hit the MDM sync. You should see now a proper URL for the OCSP entry:

My SCEP configuration profile shows pending and is not applied?
The SCEP configuration profile depends on the Trusted Root certificate profile. Assign both profiles to the same AAD user or device group to make sure the user or device overlaps and both profiles are targeted to the device. Don’t mix user and device groups. If you see pending as status for the configurations profiles in Intune for a long time, the assignment is probably wrong!
My SCEP profile settings are not recognized in the deployed certificates?
This is because some settings are mandatory set by SCEPman, the yellow rectangle is automatically set by SCEPman (for better visibility I recommend to set the settings in the yellow rectangle to the SCEPman mandatory settings like shown below). Hereby is the Key usage set to “Digital signature” and “Key encipherment”. The validity period is set to fixed 6 month currently. The red rectangle are settings which are free to modify. Long term all settings will be supported for configuration. There is a dependency on the {{AAD_Device_ID}} in the subject name, which is used as a seed for the certificate serial number generation. Therefore the subject name must include {{AAD_Device_ID}} for device certificates and for user certificates “common name including email”. Keep an eye on the subject name format in regards to the allowed characters, have a look here Create and assign SCEP certificate profiles in Intune for more details.

SCEPman editions
SCEPman is available in two different editions. If you consider a large scale enterprise deployment with professional support and maybe load balanced service you should consider to use the paid SCEPman Enterprise Edition.
If you are a geek or technical pro and you are going to self support the installation there is the free SCEPman Community Edition (CE). The free SCEPman CE is not backed by professional support services. The only technical difference is that SCEPman CE does not support redundancy through Azure Traffic Manager (no support for Azure WebApp custom domains).
Final thoughts
I hope this will lower the burden to move components to the cloud as you are now able to get device certificates easily without complex on-premises PKI infrastructure. Go and start evaluating this great solution which completes the cloud story when using a cloud-only modern management approach.
If you want to learn more of the SCEP request and renewal process see here:
Deep dive of SCEP certificate request/renewal on Intune-managed Windows clients

Hi is there anyone here offer consulting services of getting an NDES/SCEP solution deployed. I’m trying to use CBA authentication, yet i”m getting prompted for passwords.
Hey newpotato,
you can go to http://www.glueckkanja-gab.com the company I work for and request support/conuslting for SCEPman especially if you plan to buy Enterprise Edition…
best,
Oliver
Hi Oliver,
Great article, lovely and clear.
I tried to set up SCEPMan trial in two tenants yesterday both of them didn’t error but also didn’t create the App Service. I can’t see a failure in the logs. The Azure screen where the Azure AD app registration details for SCEPman are entered looks a little different (select the app rather than enter the ID), don’t know if that has anything to do with it.
Any idea?
Arran
Hey Arran,
sorry for the delay, there was/is an error with the Marketplace publishing right now. It is addressed and should be fixed soon. For the time being you can deploy the solution via the Enterprise Guide (use this link: https://docs.scepman.com/scepman-configuration/deployment-options/enterprise-deployment) which simply uses the Azure ARM template. On the mentioned guide you will find a Deploy to Azure button. The Browser should be in logged into your target tenant. The end result is similar, you simply have to provide some more info during deployment. Let me know if you have issues and I will help out.
best,
Oliver
I assume I will need a scepman generated certificate for the freeradius server. how do I get that, or if that doesn’t work, how do I upload my own ca into scepman?
Outstanding howto, by the way. Very clear.
Hi Ray,
scepman does not issue server certs but you can use an intermediate certificate if you like. Follow this guide https://docs.scepman.com/scepman-configuration/optional/intermediate-certificate.
But in general, you can also use a paid certificate for the freeradius or let’s encrypt, I guess.
But even way more convenient you can try out the Radius-as-a-Service (https://www.radius-as-a-service.com/), which can be setup in minutes and works perfectly together with scepman.
best,
Oliver
Hi,
We have Aerohive Access points in our Corp office which talks to the onprem NPS server to look for authentication.
Can you please tell me how this will work for my setup.
My client is not approving to go for Scepman’s Radius as a service plan.
Hey Ashish,
I’m not that deep in Radius solutions but as far as I understand NPS it needs a local AD and users and/or device object there. If you are using SCEPman with AADJ devices you don’t have device object in the local AD and therefore NPS can’t validate the requests. So, I guess you need a different RADIUS solution for that.
best,
Oliver
In my testing authenticating device or user object needs to exist in AD, be not disabled and Scepman CA needs to be in ntauth certificate store in AD for NPS to accept certificate login.
I have working setup where user is synced from AD to AAD but computers are AADJoined, it works with user authentication.
I guess it may be possible also to use Azure AD Connect device writeback and authenticate against those objects.
Totally agree(!) user auth should not be the issue, device certs are more an issue. If you have the chance to accomplish this with device writeback it could work, even creation of dummy object could work imho. But all this is not that straight forward as NPS is an on-prem technology. Other radius servers like Cisco ISE/Radius-as-a-Service/Meraki/etc. don’t need that much on top of it..
Hi Oliver,
Thanks for always putting out good content.
I have tried the SCEPMan, and it works fine as expected.
However, one thing I noticed is that the pattern for the CA includes the Tenant ID as OU. Is it possible to use a custom pattern so we don’t expose the CA since the portal is “public”.
Also, I am thinking about using a App Proxy in front with pre authentication, it would allow us to use Conditional Access with device registration to protect that page.
Thank you,
Hi,
The tenant id is nothing to protect, in fact it is anyway public visible/available. Look here: https://www.whatismytenantid.com/ type in the domain and get the tenant ID, nothing easier than this. Also protecting the complete endpoint will break SCEPman as the endpoint needs to be public for devices to request certificates. The request will be checked but the endpoint in the first place must be public accessible ant not CA protected, this would defeat the purpose. What you can do is, deactivate the Status Homepage for Browser access via this: https://docs.scepman.com/scepman-configuration/optional/application-settings#appconfig-anonymoushomepageaccess. It will not deactivate the API but the status page. But again, nothing on it is sensitive information. Tenant ID is not sensitive and easily to retrieve for any M365 domain.
best,
Oliver
Hi Oliver,
Perfect, thanks for the great explanation, very much appreciated.
Thank you,
Hi Olivier. Great tutorial, helped me a lot!
I have SCEP working now, the clients are receiving device certificates. Now comes part 2, which might be a bit out of scope. But i’m stuck here so maybe you can help. I have a Fortigate firewall with SSL VPN (Azure MFA) setup. Now I want to add the client certificate check. I’ve already installed the root CA certificate on the Fortigate, but don’t know what to do next. Am I correct to understand that the Fortigate should contact SCEPman to check if a client certificate is still valid? DO you happen to know how to configure this?
Hi Mark,
actually I’m not so familiar with VPN implementations. I’m sad I can’t provide some helpful insights here. From theoretical aspect you are right but I’m not aware how to realize it with Fortigate. I think you have to dig into the Fortigate docs to find out… The other way would be to consider buying the Enterprise Edition and consult the official SCEPman support. You could also check upfront if they can guide you before licensing the Enterprise Edition.
best,
Oliver
Hi Mark, I believe it comes down to if Fortiget supports OCSP for certificate validity check. I had similar issue where Azure AD only supported CRL instead of OCSP, therefore I couldn’t use Scepman.
Hi Mathieu, in which use case was this exactly? Never seen CRL only checks lately?!
Many thanks.
Hi Oliver, it was certificate based auth with exchange online. Last time I tried it was about 12 month ago and Azure AD only supported CRL not OCSP.
Ah okay many thanks for the info. I‘m also not sure if this is possible right now. Good to know! Thanks.
Hi Oliver, we’re actually trying to deploy the SCEPMan Solution und facing the following Error: “{“code”:”InvalidTemplate”,”message”:”Deployment template validation failed: ‘The resource ‘Microsoft.Resources/deployments/pid-a262352f-52a9-4ed9-a9ba-6a2b2478d19b-appSvc’ is not defined in the template. Please see https://aka.ms/arm-template for usage details.’.”}”
Any Ideas ?
Thanks in Advance.
Regards
Marcus
We are fixing it right now. As soon as it is live I‘ll let you know 👍
Hey Marcus,
we fixed the marketplace solution, but due to submission and publishing processes from Microsoft for the Marketplace it generally takes some time to appear for the public. We expect it tomorrow to be live. That’s based from our experience from the past.
In the meanwhile, you can use the Enterprise Deployment, this is not bound to the Marketplace and uses the fixed ARM template directly. Here is the documentation for this deployment: https://docs.scepman.com/scepman-configuration/deployment-options/enterprise-deployment
If you have further questions or issues don’t hesitate to contact me or glueckkanja-gab directly, have a look at the FAQ section for submitting a request if you like.
best,
Oliver
Hi Oliver, unfortunately we still cannot deploy via Az Marketplace – tested it on Weekend and again this Morning (same Error Message as posted above).
As we want to deploy the Community Edition, the ARM Deployment doesn’t seems to be functional (stated in the article its only for Enterprise Edition).
Regards,
Marcus
Hey Marcus,
you can use the Enterprise Deployment plan with the Community Edition as well. The application is the same you deploy it will switch to Enterprise Edition just by entering a Enterprise key. So give it a try. I’m very unhappy that the submission for the fixed package is still not approved by Microsoft. We will see what we can do to accelerate the publishing by Microsoft. Thanks for your patience.
best,
Oliver
Great article, but im a little confused if we can use SCEPMAN for user based certs and 802.x wifi authentication with a Windows NPS Server. My issue i have is with EAP-TLS i need to choose a certificate to apply on the NPS server but unsure which certifiate i should be using for this..
any ideas?
NPS with user certs can work…
https://docs.scepman.com/nac-configuration/nac-configuration#microsoft-network-policy-server-nps
If TLS needs a server certificate you are currently not able to request a server cert from SCEPman, but keep an eye on the upcoming versions we will add support for this scenario.
I tried these steps but I keep receiving “Unable to fetch the tenant id”. I repeated the process multiple times with no success
Sorry vacation mode was on :-), is this still relevant?
Thank you, Oliver! I successfully deployed device certificates but now struggling with user certificates. I used the same “configuration profile” as “device certificate” but changed the scope to “user certificate type”.
I’m getting error 5xx for all users, any advice?
Thank you!
Hey Joe,
Where are you seeing this error? In Intune or on the SCEPman app service side?
How is your assignment for the trusted root and config profile? they both should have the same group. user cert is best with user groups and this means user group for trusted root and for the config profile. If assigned like this there will be no issue from Intune service side during evaluation if the scope of both profiles is assigned to the targeted user.
best,
Oliver
Thank you for your reply, Oliver,
I was able to download new kudu logs and there I saw this line message:
[Error] Scepman.Core.CertificationAuthority.AbstractCABackend: Subject or SAN must contain the device’s ID or the SAN must contain user’s UPN. Could not find one of these values and therefore could not identify certificate requester.
I then edited the device profile and added the UPN variable to the san.
Couple of hours after that all user certificates were deployed.
Thank you!
May I know any use case that you have been deployed with Cisco ISE 3.1 in 802.1x for WIFI authentication. I can’t find any info how to sign the CSR request for ISE from SCEPman. thanks!
There are companies using SCEPman with Cisco ISE successfully. We also have identified during their usage some OCSP issues, as ISE sadly does not really support HTPP 1.1 and is facing issues with host headers see here: https://docs.scepman.com/other/troubleshooting/cisco-ise-host-header-limitation
If you need assistance in configuring the Cisco ISE for SCEPman usage I suggest to get in direct contact via https://glueckkanja.zendesk.com/hc/en-us/requests/new
Do you have any advice or information on how to setup SCEPman with FortiGate firewall?
We’re trying to use SCEPman with FortiGate firewall VPN (IKEv2) and machine certificate authentication. The clients connecting are using Windows 10 native VPN client with configuration profiles deployed via Intune. We have successfully setup SCEP certificate profiles with SCEPman in Intune and certificates are successfully deployed to the clients.
However, we’re not sure on how to get a CSR from the firewall signed by SCEPman. We have imported the SCEPman root without problem.
Hi,
SCEPman is not capable to create server certs in this version. We have an upcoming version 2.0 which will be able to create server certificates. https://docs.scepman.com/other/changelog#2.0-soon-in-preview
Keep in mind that the server certificate creation in 2.0 is an Enterprise feature. An alternative would be to give the FortiGate an official certificate like “let’s encrypt” or an official one from DigiCert or any other public CA.
best,
Oliver
Hi Oliver,
that is great news, thank you for the feedback.
Hey,
Thanks, here I found about the UPN trick on the Android Enterprise. I was using DNS SAN.
However, the SCEP certificate is still installed as VPN and APPs and Intune pushes two weird certs for Wifi with the SSID name. Is this expected? What are these certificates?
Hey rgomez,
So, you deploy one SCEP profile and you get 3 certificates? Do I understand this correctly?
Best,
Oliver
You can no longer select the Azure Active Directory Graph as an API permission. Is there a work around for this?
Hi, please refer to the docs.scepman.com website for up to date information about app registration. For SCEPman 2.0 you don’t even need the registration info as it can also be installed via managed service identity.
Best,
Oliver
Hi, I’m testing this out for a scenario where we want users to be able to onboard themselves with autopilot though VPN.
During Autopilot only the Scepman root cert is succesfully deployed. The client device cert fails. Do you happen to have a clue on this?
It works fine when deploying the certs to existing HAADJ devices
This should not be an issue honestly. I do device cert deployments in Autopilot scenarios all the time. device and user certs actually. Do you still experience the issue?
Do you know when a keysize of 4096 will be available in MEM/Intune SCEP.
Sorry I’m not aware when they will support 4k 🤷♂️
Thank you for this great article and solution – I was able to spin up the community edition without any issues and looking forward to get rid of our current ancient AD-integrated PKI/SCEP setup.
I do have one question though regarding the interaction between SCEPman and Intune – in the absence of a shared SCEP request password, what is stopping another Intune Admin from taking my SCEP Enrollment URL/Root CA Cert and using it in an Intune SCEP profile in his Intune tenant (and thus enrolling Certs from my SCEPman instance)? I seem to miss a basic concept here that prevents such a scenario. Maybe someone can enlighten me 😉
Hey Stefan,
you might want to have a look here: https://oliverkieselbach.com/2022/09/21/deep-dive-of-scep-certificate-request-renewal-on-intune-managed-windows-clients/#ChallengeValidationByIntune
So basically, Intune sends out the challenge and the device sends it to the scep server, the scep server again sends it to intune vor validation, this includes the device id, profile etc and this is validated. So, the scep server can talk only to the registered intune tenant he belongs so if someone generates a challenge from a different tenant the validation route is broken as the scep server would not send it back to the initial creator it would send it to the registered intune tenant he belongs and this instance would deny the request as it is not from himself. No device id match, password, profile etc.