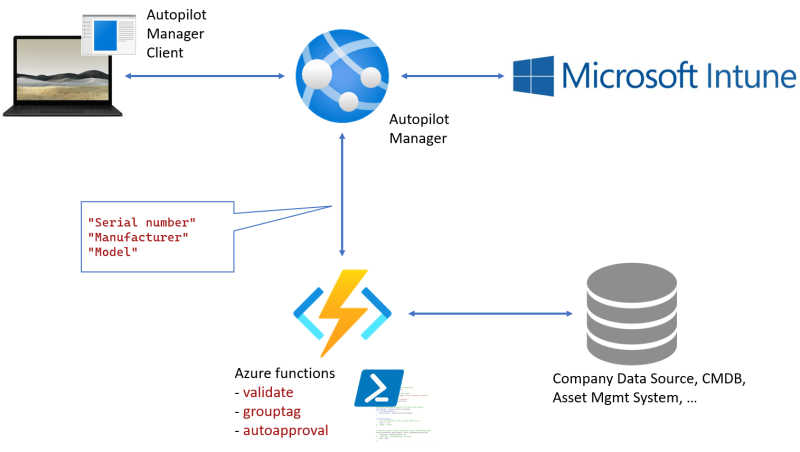
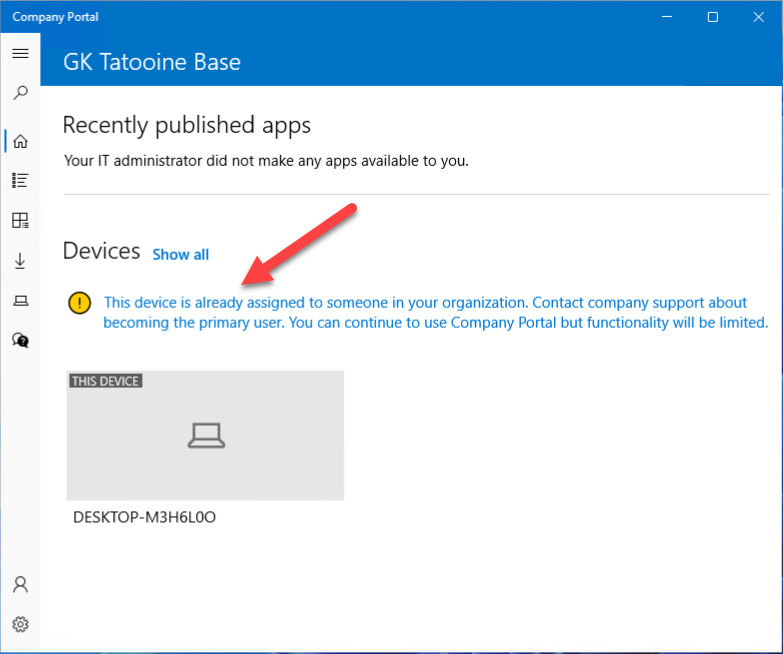
New enhancements to Autopilot Manager are here. This time I focused on further optional automations of the import process based on customer feedback. Another year is gone and Autopilot Manager once again gets new features. Ironically last time I introduced new features (Evolving Autopilot Manager) was also ~1 year after the initial release. So here…
Read More