A year ago I explained the policy processing in Windows 10 with Intune with the following article:
Intune Policy Processing on Windows 10 explained
At the time of writing the behavior of most Configuration Service Providers (CSPs) followed a tattooing model. Meaning once a setting got applied it wouldn’t change until you explicitly set a new value for it. Just the simple removal of the policy resulted in a tattooed setting, still active on the device.
This behavior changed lately (Windows 10 version 1903, 1909 and 2004 partially verified) and we do not have tattooing in general with all the CSPs anymore.
Quote from Assign user and device profiles in Microsoft Intune:
When a profile is removed or no longer assigned to a device, different things can happen, depending on the settings in the profile. The settings are based on CSPs, and each CSP can handle the profile removal differently. For example, a setting might keep the existing value, and not revert back to a default value. The behavior is controlled by each CSP in the operating system. For a list of Windows CSPs, see configuration service provider (CSP) reference.
To change a setting to a different value, create a new profile, configure the setting to Not configured, and assign the profile. Once applied to the device, users should have control to change the setting to their preferred value.
When configuring these settings, we suggest deploying to a pilot group.
This is an important fact to know and really worth a post to make everyone aware of this. The behavior of MDM policies now is more or less the same like the GPO policy processing. We got all missing parts which were not available in the first implementations of MDM management on Windows 10. Especially we have enforcement as shown in the previous article and removal on un-assignment. Keep in mind that every CSP is responsible for the new behavior and there is not a compiled list which CSP supports and implemented the new behavior. Maybe we can compile one as a community. I started a list in the end of the article.
To demonstrate this new behavior, I picked 3 different CSPs which are commonly used and checked if they are removed from the system after un-assignment. I’ve chosen the Policy CSP, Network CSP, and Defender CSP to verify the behavior on a Windows 10 version 1903, 1909 and 2004 device. Other Windows 10 versions still need to be verified. Will be interesting how far this is backported, my guess is max to Version 1903.
Let’s start by configuring settings from each CSP. I’ve created a Device Restriction profile and configured to hide Ease of access from the Settings menu which utilizes the Policy CSP in the background:

Just for reference, this is how the ease of access looks like before applying the policy on a Windows 10 Version 2004 device (same device is used for all screenshots):

Then I’ve chosen to configure the Network Proxy setting to disable auto detect of proxy settings which uses the NetworkProxy CSP in the background:

Again for reference this is how it looks like before applying the policy, Automatically detect settings is turn on:

Finally, I’ve chosen to apply a Defender policy which utilizes the Defender CSP to submit samples automatically:

This is how the Defender setting looks like before applying the policy:

After I assigned the device restriction profile to my test device and did a MDM sync, I can see all settings successfully applied:
Ease of Access Settings has less options:

Network Proxy automatically detect is turned off:

Defender sample submission is turned on:

So far so good, everything went as expected. Now we simply un-assign the complete device restriction profile by removing the AAD device group I used for the assignment:

After a short wait and clicking on MDM sync again, we should see every setting removed and all UI elements are accessible again with their default values.
Et voilà – everything removed and back to defaults, see below!
Ease of access settings are available again:

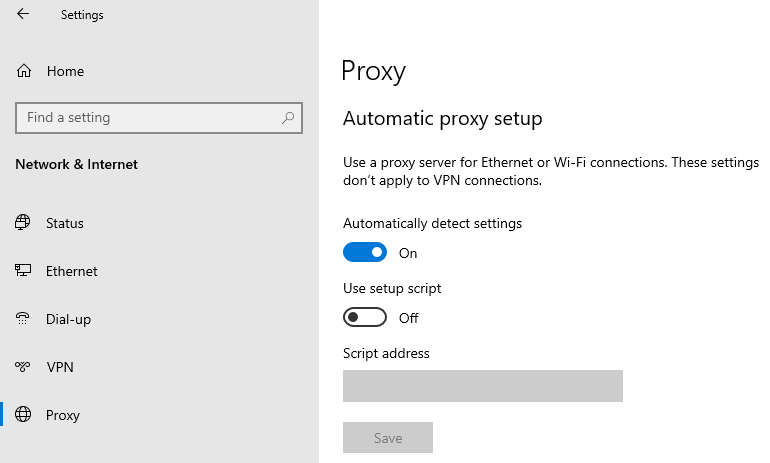
Network Proxy auto detect setting is available and turn on again:
Defender Automatic sample submission can be configured by the user again:

I did the same test by not just un-assigning the profile, I switched the values back to “Not configured” and this gave me the same results. So, un-assignment and “Not configured” will revert back to defaults like we used to have with GPO policies (okay there are also some policies in GPO which do tattooing :-)).

This is an important feature to know, especially when troubleshooting the behavior should be crystal clear to everyone!
More technical details
I assume the implementation is realized by supporting the Delete command from SyncML Protocol (see also my Monitoring Tool SyncML Viewer) on the various CSPs. If we look at the NetworkProxy CSP for example, we see statements for supported operations. In the following case, starting with Windows 10 version 1803, the Delete operation is supported for ProxyAddress on the NetworkProxy CSP:
https://docs.microsoft.com/en-us/windows/client-management/mdm/networkproxy-csp
ProxyAddress
Address to the proxy server. Specify an address in the format <server>[“:”<port>].
The data type is string. Supported operations are Get and Replace. Starting in Windows 10, version 1803, the Delete operation is also supported.
I think this is the key functionality involved here, support for delete on the CSP and of course the MDM server in this case Intune has to send the Delete command to the client on un-assignment or configuration of “Not configured”.
If we have a look what happens on the client side if we un-assign the policy to hide Ease of access from the example above, you will see the Event ID 819 MDM PolicyManager: Delete policy, Policy: (PageVisibilityList), Area (Settings). This clearly references the setting we configured earlier, which gets deleted here:

To summarize, we have seen Windows 10 version 1903, 1909 and 2004 does a settings removal when policy is unassigned or set to not configured. I already tested the following CSPs, others still need to be tested for this behavior:
- Policy CSP
- NetworkProxy CSP
- Defender CSP
- Update Ring Policies (during my tests removal worked only with 1909+)
As already mentioned in my previous article and following the Microsoft docs article (Troubleshoot device profiles in Microsoft Intune) these CSPs are also using the same behavior:
- Wi-Fi profiles
- VPN profiles
- Certificate profiles
- Email profiles
I’m happy to add new ones if someone verified the new behavior already for them.
That’s it for now, always make sure to understand the “inner workings” of technology to successfully implement and troubleshoot it.
Finally something also worth to mention when working with CSPs is the reboot behavior of CSP settings, when device based assigned and applied during Autopilot/ESP. Read my MVP fellow Jörgen Nilsson’s blog article here:

thanks Oliver – I will try to contribute to the list 😉
Perfect thanks!
Thank you for the post!
This is applied to Update Rings also?
I have some machine that have the policies applied but are not following for example the federal days.
Hi Sidnei,
yes at least for 1909 and 2004 I verified it and it worked flawlessly. Un-assigned the Update ring policy and the settings got removed again from the device.
best,
Oliver
You are a giant in the Intune community.
Great info
:-), thx buddy I‘m glad you like my work!
Oliver, thanks for your contribution.
I have an issue that I’ve restricted(Blocked) “Removable storage” to a user. Worked perfectly. Then I removed that user and restrictions. Synced policy Intune management extension and sync itself. I’ve rebooted multiple times and synced again.
Even though the user is no longer under the “blocked” policy he still cannot access any removable storage.
Based on what you mentioned above I don’t think it works for all restrictions.
I might be wrong. Something you can shed light on?
Thanks
Hey Ari,
sorry for my delay. Yes it is not fully implemented for every CSP. So you might have found one which is not currently supporting the removal. Sadly there is no official documentation on this. It is more an try and error game to find out what is working and what not. In your case I guess you can fix the device by creating a small PowerShell script which reverts the settings on the effected device back to dfaults.
best,
Oliver
Oliver, thanks for responding back.
Unfortunately there is nothing documented on this feature (block Removable Storage). I’ve been working with MS for the past 3 weeks and they cannot figure it out. I have several production devices that I enabled this feature on. Now I’m trying to reactivate removable storage and I can’t. I even disconnected/removed the device from the domain and tried with a local admin user and removable storages are still blocked.
It seems that the only option is to format the device.
Moving forward I might just create my own PS that blocks removable storage and when I need to enable removable storage I’ll push another PS to enable removable storage.
Would love to hear if you have any experience with this, blocking removable storage via Intune. Any PS scripts you can share..
Thanks again.
Oliver, thanks for your contribution.
I have an issue that I’ve restricted(Blocked) “Removable storage” to a user. Worked perfectly. Then I removed that user and restrictions. Synced policy Intune management extension and sync itself. I’ve rebooted multiple times and synced again.
Even though the user is no longer under the “blocked” policy he still cannot access any removable storage.
Based on what you mentioned above I don’t think it works for all restrictions.
I might be wrong. Something you can shed light on?
Thanks
Hi Ari,
just want to let you know that we have the same issue here since we started with OnlyAzure-joined clients 2 years ago.
We set the device restriction config profile “Removable Storage”=Block by default and unblock them with an excluded group.
In general this works fine, the change between block and unblock works also multiple times on a device. But on a few devices (I estimate 1% of the clients) the unblock is not possible. We tried a lot but no solution except complete reinstallation.
We also figured out that the restriction modify a reg key
(HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\System –> AllowStorageCard) but a manual change back didn’t unblock the machine.
Whenever you got a solution, would be cool when you share it here. I will do the same.
Raphael
Raphael,
So after a month and a half, and multiple MS support reps, they came back with, “unfortunately there are some settings that cannot be reverted. The documentation is not clear. Once you apply this setting you will need to format the device to remove restrictions.”
I’ve tried, removing it from the domain, logging on as a local admin.. Nothing.
I ended up formatting the device. Luckily for me I ran a test run with one device so my production devices were not affected.
I found other ways to apply the restriction. I created an app with an install and uninstall .cmd file that applies a reg tweak. This way I can remove the reg tweak via Intune and it will run the “uninstall.cmd”
I hope I was ale to help.
Hi Raphael,
We have the exact same issue here just now. Did you ever find a solution? I’m hoping we can avoid having to re-image the affected machines here. As you say it’s a small percentage of machines that are affected, so I’m hoping there’s somewhere in the client that we can force a change to resolve.
Thanks,
Si
Si, Unfortunately no. M$ said, there are some settings in Intune that cannot be reverted back. After more than a month and several M$ Intune specialists later, the only resolution is to format/ re-image the device.
Yes I agree, it sucks.
Most of the Intune policies management is just plain awful, inflexible, bad reporting, Nothing like good old GPO that simply worked
With some settings/scripts if you get them right bang on first time, they might work, but if you need to rerun something, OMG, that is a fuff to get it corrected, it will fail, it will not apply etc. Just a nightmare
Unfortunately, the Network Proxy settings are not applicable to Windows 11 Multisession…. Trying to set system-wide proxy for Azure Virtual Desktop hosts, but alas… not applicable.