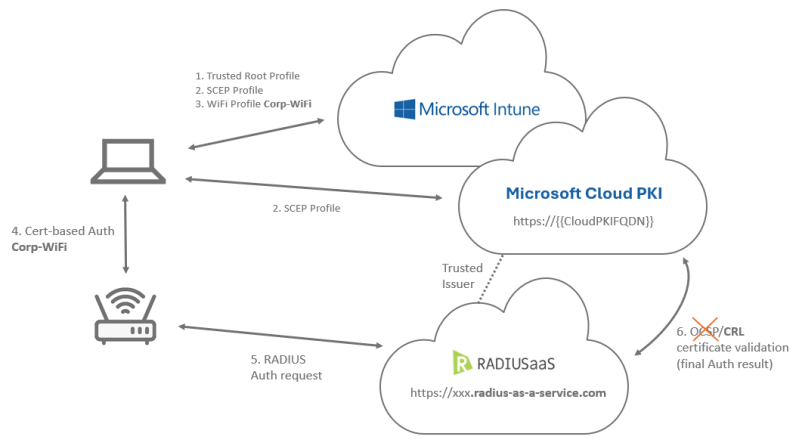
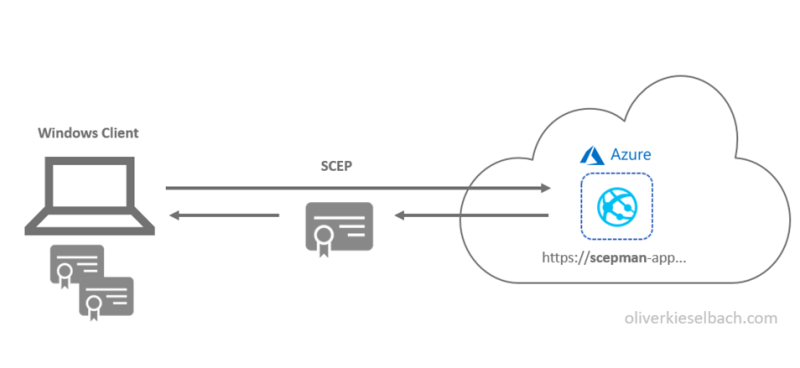
Maybe you have read the previous article How to configure certificate-based WiFi with Intune already and asked how to do the same with the freshly released Microsoft Cloud PKI. Then you don’t have to wait any longer, I promised to write about it and here is the setup with Microsoft Cloud PKI. I’ll dive into…
Read More