
This guide will demonstrate how to enable the BitLocker startup PIN for pre-boot authentication on Windows 10 with Microsoft Intune. I will walk through how to accomplish this in a nearly fully automatic way. Let’s start with some facts around BitLocker to understand the technology more precisely. In fact, I think a pre-boot startup PIN is not always necessary. To explain my point of view a bit further, we need to have a more detailed look at the encryption key material handling of BitLocker. The key material security is based mainly on the trusted computing platform concepts. Easy speaking this is the protection of the key material with a TPM (aka TPM only scenario) or with a TPM and pre-boot authentication startup PIN (aka TPM+PIN scenario).
How does BitLocker key protection work?
First, we need to understand the general procedure of how BitLocker will get access to the encryption key. The Trusted Computing Group introduced the trusted computing platform. In short, this board defined measures for trusted computing. From interest here is the Endorsement Key and the Sealed Storage concept. The underlying idea is to bind private information to the platform configuration to generate the Sealed Storage. The platform configuration includes hardware and software which is being used. The concept of the endorsement key is simple. It is a generated key during manufacturing time on a chip. The key cannot be changed and will never leave the chip. In general, both these concepts are widely known by people in the form of the Trusted Platform Module (TPM). The TPM has an endorsement key and can only be accessed from unmodified and untampered hardware and software configuration.
In a widely used standard configuration of Microsoft Windows 10, BitLocker is used with a TPM only key protection to protect BitLocker key material. As already explained Windows uses so called platform configuration registers (PCRs) to measure the state of hardware and software configuration (compare article TPM platform validation profile) and releases the key material in an unmodified and untampered configuration is available. We can easily say the integrity of the configuration is proven and therefore the key material is released for BitLocker decryption usage. This leads to a situation, that an attacker needs the complete hardware and can’t modify the platform configuration otherwise the key material is not released. Even in case the complete hardware is stolen, the device might reach the platform configuration state to boot up, but only until the normal Windows logon. At this point in time the attacker needs to overcome the Windows logon which is protected from brute force attacks by slowing down logons retries, in case of unsuccessful logons. In fact, this is a pretty safe configuration to run Windows 10 with BitLocker protection.
No downside at all?
Not really, there are always bypasses in various IT systems and this is true for this BitLocker configuration as well. The fact, that in case of an unmodified platform configuration, the key material is released and put into memory for cryptographic operations can be used for various attacks.
Attacks by accessing the memory in various ways can finally give you access to the BitLocker key material. For example, Direct Memory Access (DMA) ports and Plug and Play mechanisms are used to gain access to memory during Windows run time (aka side channel attacks). But also, the fact that cooled down transistors are not losing their programmatic state immediately, can give the attacker enough time to dump the memory and get BitLocker key material. The latest attack was done by using electric engineering tools like oscilloscope and logic analyzers to read the signals directly from the wires/bus (aka TPM sniffing). For interested readers I recommend reading – Extracting BitLocker Keys from a TPM.
Do I need to worry now?
I don’t think so! Security is always a cat and mouse game, attackers getting better and defenders build better protections. Attacks against BitLocker key material and the platform exist, and new ones will likely be found in future. In the meantime, you must think about who you want to protect your data against. If you target nation state hackers, I don’t think that all this is enough as data will be exfiltrated in some way anyway. If they can’t easily target your device, they will have a complete suite case full of options to accomplish their goals and finally get your data.
Security is about building defense lines and this involves different areas and different technology to finally operate a secure enough but still usable system. I will explain this by using an example. We can choose our hardware wisely to eliminate some side channel attacks in advance. In fact, the Windows 10 hardware certification program makes sure some of these attacks are eliminated by the design of modern hardware. Second, we build several layers of protection around our data. This includes full disk encryption (FDE), state of the art security configurations in Windows, anti-malware protections which can respond immediately in case of threats and malicious behavior, and entity security by encrypting important data individually. The overall security posture of your device (and of course the used services, but these are not in scope of this article) define a successful defense strategy. A well-designed workplace solution and the services around it, with the right principles, will give the average and skilled attacker a hard time as the defense layers are able to counter in all stages of an attack.
Additional countermeasures?
The BitLocker standard configuration in combination with other security measures will balance convenience in usability and security (please also read the Microsoft article BitLocker Countermeasures). If you think your protection level is not enough and a good overall solution can’t be accomplished in your setup, and you want to bolster your security by introducing pre-boot authentication with an additional PIN, the following guide is right for you. The additional PIN requirement during startup adds a kind of control gate to the TPM operation. The new procedure with a startup PIN is as follows. The TPM will not release any key material since the platform integrity is verified and in addition the startup PIN must be entered. Without successful PIN entry during early startup phase, the TPM will not release the key material and therefore no key material will be loaded into memory, which renders most cold boot attacks useless. This is an example of how a BitLocker pre-boot authentication startup PIN looks like:
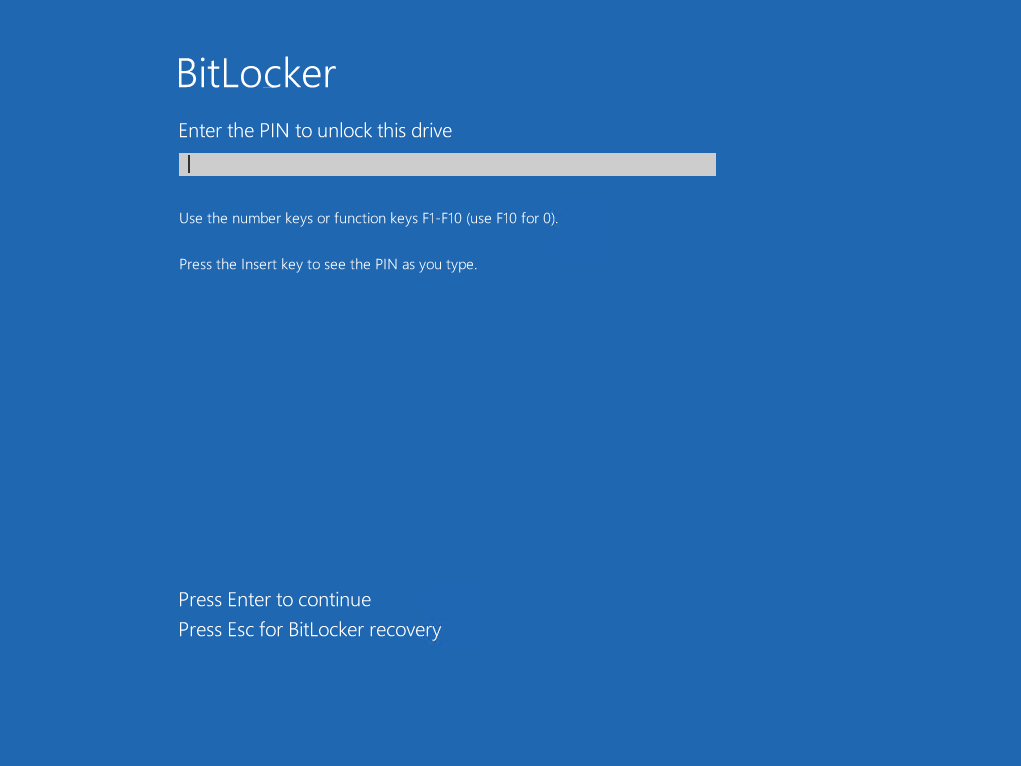
Challenges while enabling TPM+PIN with Microsoft Intune on Windows 10
In my guide Enabling BitLocker on non-HSTI devices with Intune I’m essentially describing how to implement BitLocker encryption on Windows 10 devices with Microsoft Intune for all your devices, even the ones not holding special hardware certifications (HSTI). The guide shows the Microsoft Intune configuration profiles and how to achieve this in a automatic and silent way. The result is an encrypted OS disk without any interaction with the user.
And here lies exactly the challenge when we talk about a user definable PIN. Sure, we could fall back to the Intune capabilities to trigger the BitLocker encryption wizard and not silently encrypt the OS disk. To say it in different words, enabling silent BitLocker encryption will only work with TPM only and not if you enforce a PIN. As soon as you require a PIN you must rely on the BitLocker encryption wizard and the user you must click through it.
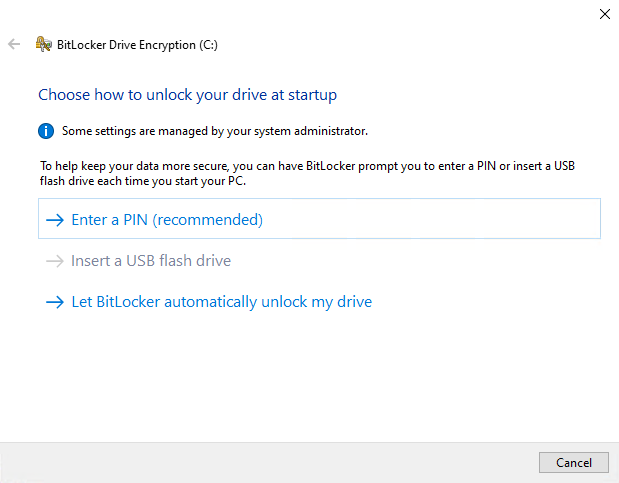
The next challenge is that we have to provide a way to do all this as a standard user. Standard user permissions are common and a good security practice. The manual way of enabling BitLocker needs administrative permissions, can be seen on the small UAC shield icon in front of the links:
The solution?
We need a way to ask the user for the PIN and encrypt the OS disk as soon as possible. The idea is to silently encrypt the disk and ask for the PIN later in the process. This way we would have a secured device right after deployment and the user must set his individual PIN afterwards. I follow the same configuration as in my last BitLocker article Enabling BitLocker on non-HSTI devices with Intune and allow “additional authentication at startup” > Allow TPM and Allow startup PIN with TPM. It is not needed to configure the “OS drive Recovery” options as the silent encryption will always backup the key to AAD. The settings below are enough to have everything in place what’s needed:
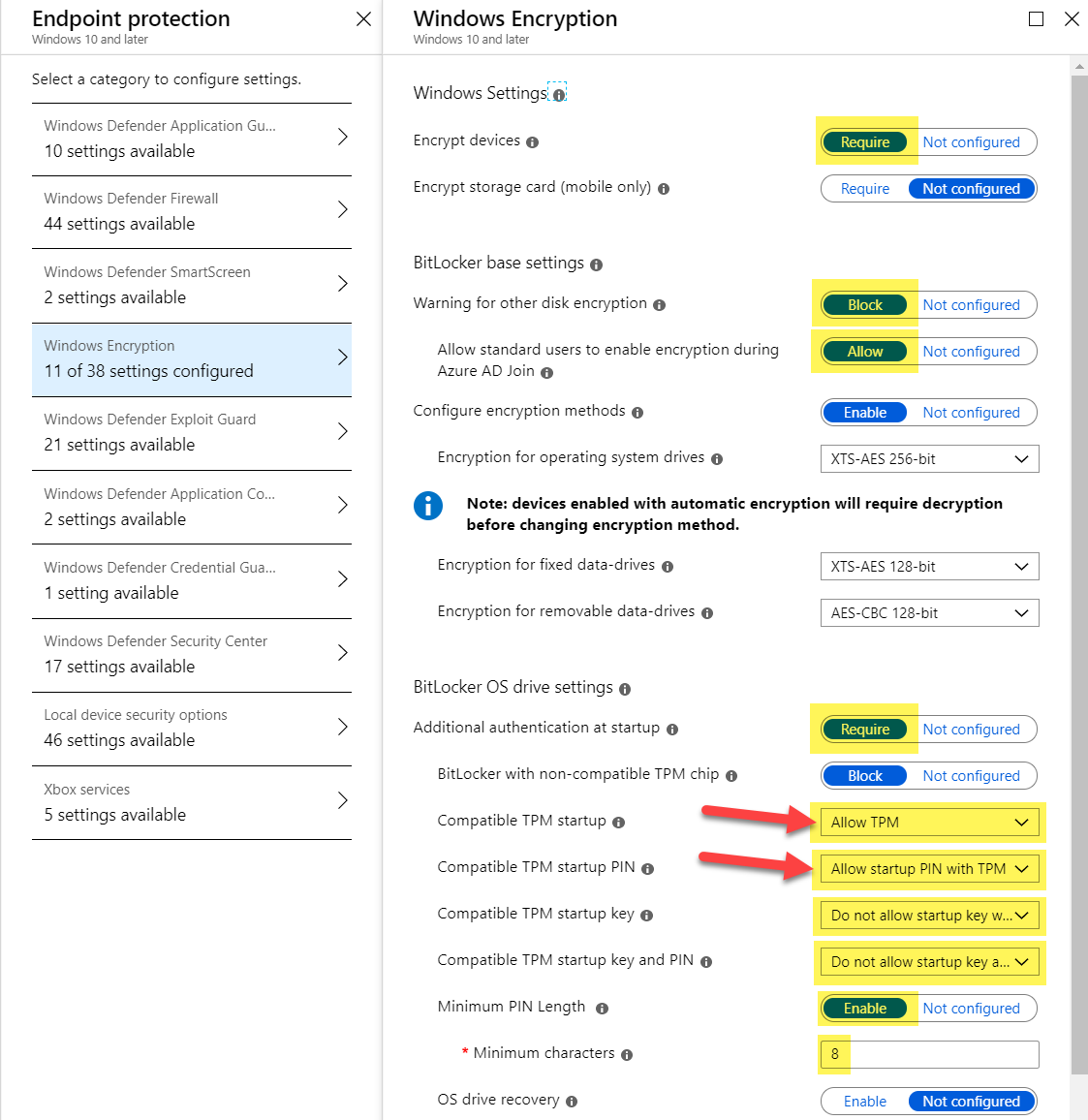
The challenge with this approach is, that we have to ask for the PIN in user context with standard user permissions and the TPM+PIN key protector must be set in system context.
I’ve created an Intune Windows app (Win32) which has a PowerShell script logic to display a PIN entry dialog and to set the BitLocker key protector TPM+PIN.
SetBitLockerPin – Intune Win32 app files
https://github.com/okieselbach/Intune/tree/master/Win32/SetBitLockerPin
The .intunewin package SetBitLockerPin can be created easily with the Intune Content Preparation Tool and the following command:
.\IntuneWinAppUtil -c .\SetBitLockerPin -s SetBitLockerPin.ps1 -o .\ -q
This way we can target the app as available to the device or user and the user is able to set the PIN as a standard user. We target the Windows app in system context for install. To escape from the system context, I utilize the ServiceUI.exe from the Microsoft Deployment Toolkit (MDT) to present the PIN dialog provided by a small PowerShell script.
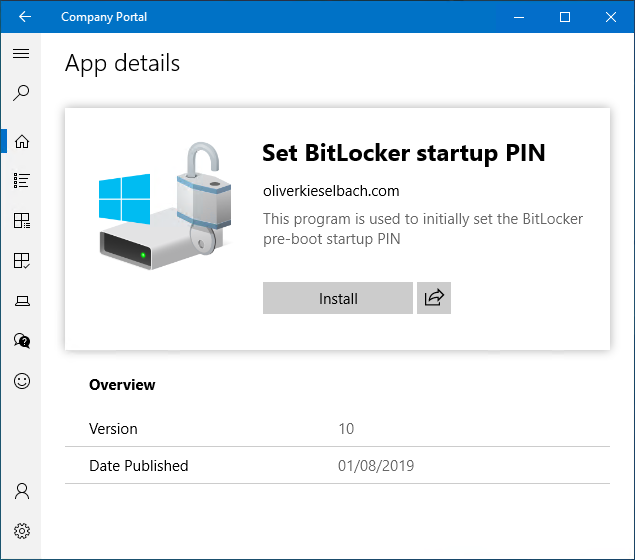
The dialog will find the configured minimum PIN length from Microsoft Intune and looks very similar to the original Microsoft Windows BitLocker change PIN dialog. I thought it helps when keeping the same style in regards of creating user adoption material later. The PIN creation dialog can be run with standard user permission as it is triggered from the Company Portal. This is how it looks like:
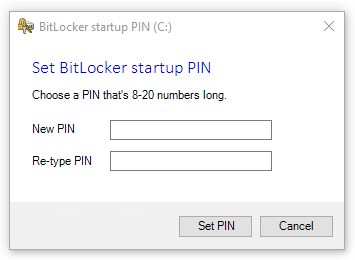
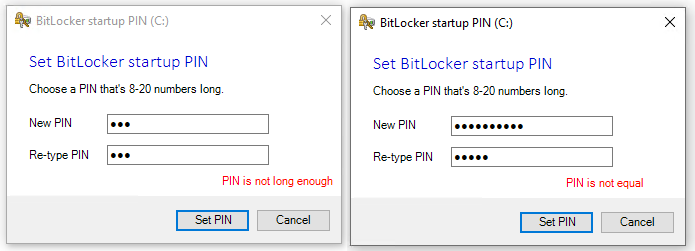
After entering the new startup PIN, the entry is passed back via a temporary file, encrypted via DPAPI to the system context. The PIN is read and decrypted by the calling script and used to configure the new TPM+PIN key protector for BitLocker. The temporary file is immediately deleted. This is an easy approach to transfer this data and the PIN itself is only short lived-in encrypted (DPAPI) in a temp file available. Basic input validation is provided like PIN length, simple PINs (1234 or 4321), and correctly re-entered PIN:
UPDATE: The dialog now even supports multi-language. There is an additional language.json file in the GitHub repo which can be used to add additional languages. The json file has sections like en-US, just copy it and change en-US for example to fr-FR and replace the English strings with French ones.
"en-US": {
"characters": "characters",
"numbers": "numbers",
"choosePin": "Choose a PIN that's {0}-20 {1} long.",
"PinIsNotEqualNotLongEnough": "PIN is not long enough",
"PinIsNotEqualOnlyNumbers": "Only numbers allowed",
"PinIsNotEqualSettingNow": "Setting valid PIN now...",
"PinIsNotEqual": "PIN is not equal",
"PinIsTooSimple": "PIN is too simple",
"BitLockerStartupPIN": "BitLocker startup PIN",
"RetypePIN": "Re-type PIN",
"NewPIN": "New PIN",
"buttonCancel": "&Cancel",
"buttonSetPin": "&Set PIN",
"labelSetBLStartupPin": "Set BitLocker startup PIN"
}
To make sure the BitLocker PIN creation dialog can only be used once I’ve created a detection logic script for the Intune Windows App (.intunewin). This small script DetectBitLockerPin.ps1 checks if the TPM+PIN protector is already set:
Write-Output $(Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where { $_.KeyProtectorType -eq 'TpmPin' }
Use the DetectBitLockerPin.ps1 as a custom detection script in Intune and use the following command for install/uninstall (I don’t have an uninstall but it is a mandatory field)
powershell -ex bypass -file SetBitLockerPin.ps1
Your app Set BitLocker startup PIN app should look like this. The image is also provided in the GitHub:
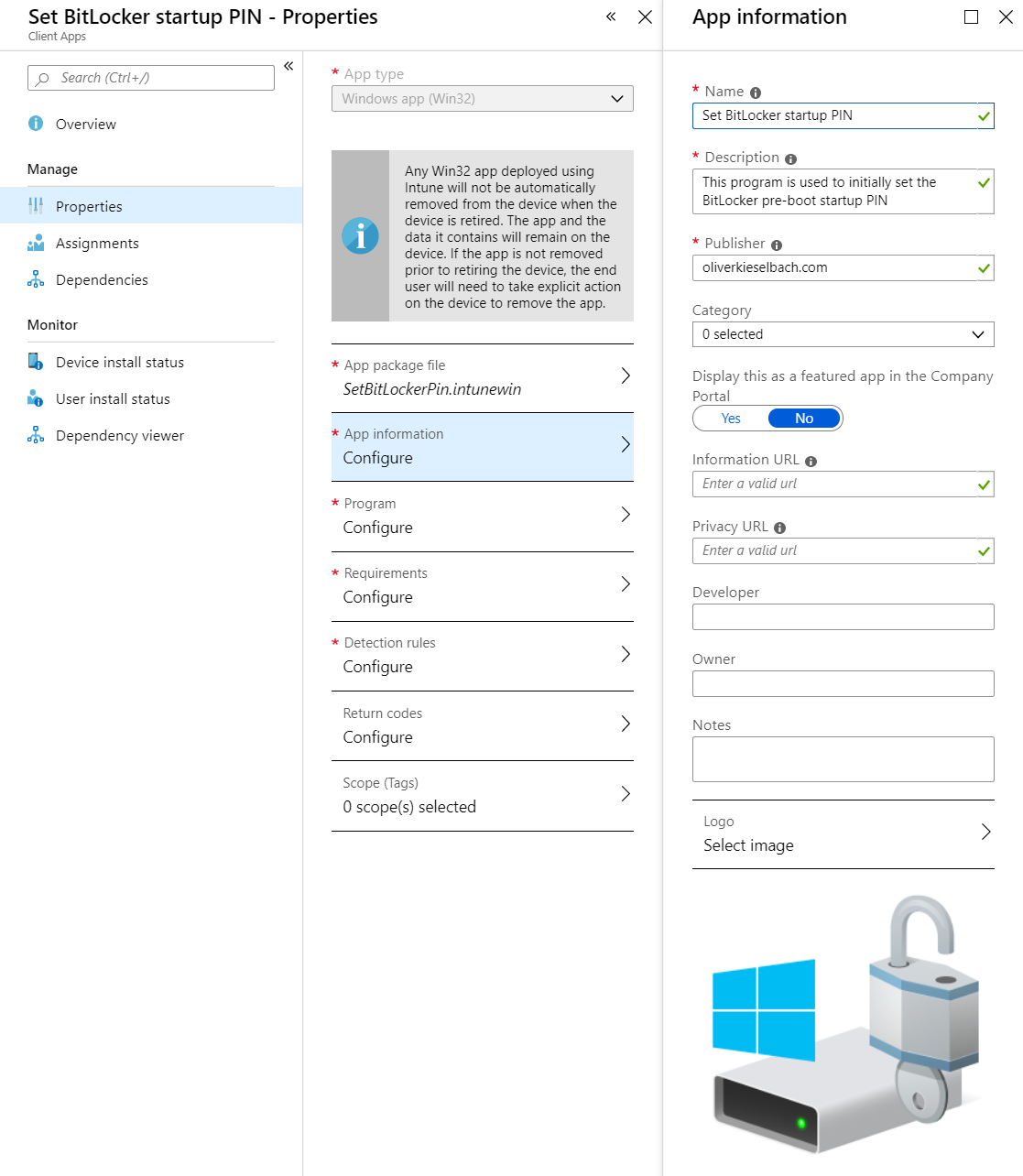
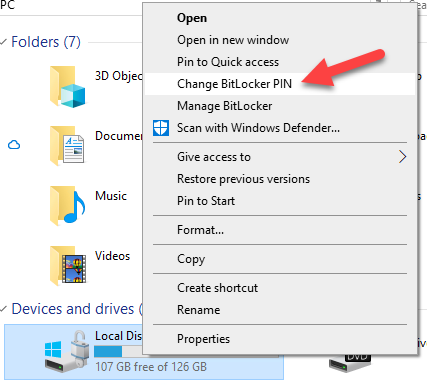
For further demonstration the very similar Windows Change BitLocker PIN dialog below. We can see it can be run without administrative permission as well:
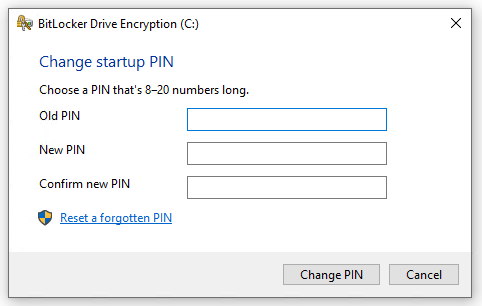
What about reporting on the Key Protector usage?
As we have no initial PIN creation enforcement here, I thought it is good to have a way, to lead your users who need additional pre-boot authentication, to set the PIN. I’ve created a small PowerShell script which will run periodically (registers itself as scheduled task) and upload the used BitLocker key protector type information to an Azure Table Storage.
The creation of the Azure Table Storage is quite simple. For a more detailed explanation have a look at my fellow Roger Zander’s blog post BitLocker management with Azure Table Storage
The upload script for the BitLocker key protector type information
https://github.com/okieselbach/Intune/blob/master/ScheduleAndUploadBitLockerKeyProtectorType.ps1
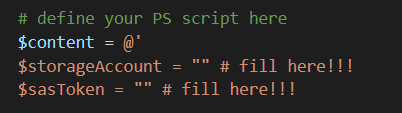
You have to fill in the Azure storage account name and the generated SAS signature for the table storage (compare Rogers post if unclear):
Upload it to Intune as a PowerShell script and assign it to your devices you like to protect:
The script will create a local script on the device and a scheduled task to run it periodically. Remember if you don’t like the script to run on your devices anymore, you have to create a uninstall script which deletes the script from C:\ProgramData\CustomScripts\UploadBitLockerKeyProtectorType.ps1 and the scheduled task UploadBitLockerKeyProtectorType.
After Azure table storage creation and PowerShell script deployment, we have an easy reporting solution if the targeted device group has set the PIN accordingly to the organizational requirement.
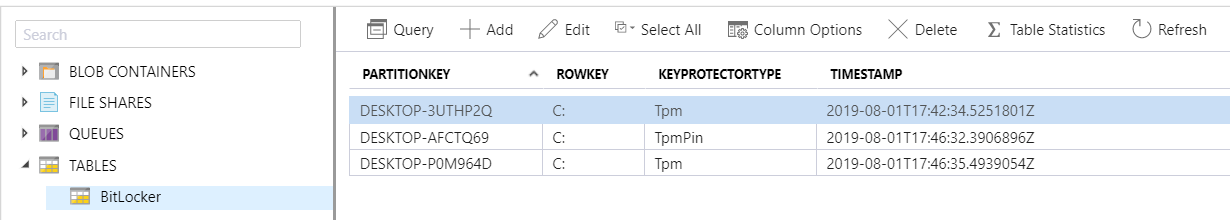
The table storage can be viewed and queried directly in the Azure Portal:
Or you connect the table storage directly with Microsoft Excel and analyze your data there:
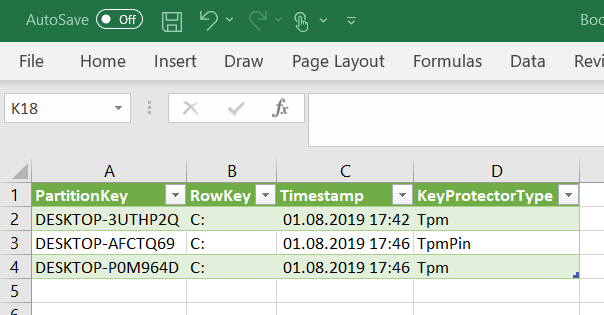
Follow the wizard and provide the Azure storage account and access key and import the table data:
What about user notifications?
To make life easier for the end users or to simply remind them to set the PIN, we can build a customized email and provide a direct link to the app in the company portal. This way the user can be targeted directly and asked to set the PIN.
First, we need to find the direct link to the app for the Company Portal. This is actually very easy but not obvious. Just use the Share button on the app in the company portal and send the information to you by email or to a OneNote:
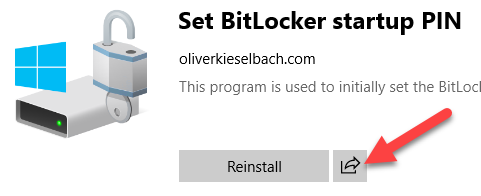
After this you will have a link with the application guid in the form:
companyportal:ApplicationId=<yourguid>With this link you can craft an email to direct your users to the app in Company Portal. Remember this special link can only be used in an email app like Outlook who displays this as an actual link. Outlook on the web will not show it as a link:
Targeting as required app
UPDATE: 14/Oct/2022
If you like to target the solution as required app, the requirement rules can help! See my article here:
Post ESP Intune Win32 apps installations
Summary
I’ve demonstrated a way to securely deploy Windows 10 with encryption and enabled easy handling to add the PIN as additional pre-boot authentication for BitLocker. Although this is a solution to set a startup PIN with Intune, I really recommend thinking twice as a PIN might not bring additional protection if the users are bugged by yet another PIN for the system. If they set them to the same as Windows Hello for Business or even worse, they write them down on a post-it and store them along with the device you have no security improvement. This would lead to a situation where an attacker has quite an easy situation, just steal the device and use the PIN written on the post-it for pre-boot authentication startup PIN and for Windows Hello for Business. This situation would have dramatically lowered your security posture, which was surely not intended. A pre-boot startup PIN can protect but should be set on systems where users are understanding the risk and actively supporting this security measure. I think for most users, security must be relatively simple, otherwise they won’t support you or even do things which will lower your security.
Thanks for reading and always think twice about security settings and how they will bring value or maybe harm your environment.

Thanks for this post! it was extremely helpful and worked a treat 🙂
Thanks for this post, worked perfectly and did exactly what I was after!
Hi Oliver,
so we have been using this but one of the issues we have found is that until the Encryption is complete you cannot install the App it will Fail (which makes sense).
Is there a better way to check Encryption complete and then run your App? Obviously this time would vary based on HDD/SDD Size. Maybe a PS Script in Task Scheduler constantly checking which would then call your Script. which if it has its Protector Detection built in it wouldnt keep prompting the user.
How do other people get around this issue of waiting for the drive to Encrypt before installing the App. relying on users checking just doesnt cut it.
Actually, I didn’t face this issue as with Azure Active Directory joined devices encryption happens during AADJ and typically the encryption process is used space only. This means when you reach the desktop the device is encrypted and the App does not fail. This is at least my typical scenario.
Hey Chris,
I faced the same problem. My solution is:
Under requirements, configure an additional requirement script to detect if Encryption is 100% done and active. My code:
$bitlockerVolume = Get-BitLockerVolume -MountPoint “C:”
$statusBitlocker = $bitlockerVolume.ProtectionStatus
$VolumeStatus = $bitlockerVolume.VolumeStatus
if ($statusBitlocker -eq “On” -And $VolumeStatus -eq “FullyEncrypted”){
#Write-host “Bitlocker active and 100% encrypted”
Write-Output 1
Exit 0
}
In this case, script output is Integer equals 1 to say “requirement is given”.
Hi Olivier, with the help of the blog of my colleague Peter van de Woude, I was able to configure a Custom Compliance Policy for the BitLocker PIN. https://www.petervanderwoude.nl/post/working-with-custom-compliance-settings/
PS-Script to be used:
$KeyProtector = (Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where { $_.RecoveryPassword -eq ” }
$KeyProtectorHash = @{“Key Protector Type” = $KeyProtector.KeyProtectorType}
return $KeyProtectorHash | ConvertTo-Json -Compress
JSON:
{
“Rules”:[
{
“SettingName”:”Key Protector Type”,
“Operator”:”IsEquals”,
“DataType”:”Int64″,
“Operand”:”4″,
“MoreInfoUrl”:”companyportal:ApplicationId=”,
“RemediationStrings”:[
{
“Language”:”en_US”,
“Title”:”BitLocker PIN must be set by the user.”,
“Description”: “Please make sure that the user sets a BitLocker PIN using the application in Company Portal.”
}
]
}
]
}
Within the Compliance Policy you can configure a Notification for the end user if a BitLocker PIN is not configured (Non-Compliant). Within this notification you can specify the BitLocker PIN application in the Company Portal.
Happy to share
Regards
Tom
PS. Remember Custom Compliance is still in preview and will be not be free to use according to documentation of MSFT
Hi,
I’ve created a similar way to doing this by using ‘Endpoint Analytics – Proactive Remediations’. Using the below as a detection script. You could also put a toast notification script in for remediation for users that have yet to set their pin.
PS-script:
$KeyProtector = (Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where { $_.RecoveryPassword -eq “” }
$KeyProtectorHash = $KeyProtector.KeyProtectorType
Try {
If ($KeyProtectorHash -eq “TpmPin”){
Write-Output “Compliant”
Exit 0
}
Write-Warning “Not Compliant”
Exit 1
}
Catch {
Write-Warning “Not Compliant”
Exit 1
}
How do you deal with devices that have ended up with multiple TPM protectors, we’ve used this and have seen devices with a TPM and a TPM+PIN protector and we’re trying to figure out what’s causing this.
Actually, I didn’t have this situation… I would try to replicate the issue and then dig into the code. hard to say what might go wrong
Hello, thanks for this Instruction. I would like to ask, about the Intune App implementation, if there has to be any specific uninstall command or detection rules etc. This would be very helpful, thanks.
Hey,
There is no specific uninstall (as I didn’t have a uninstall function, just copy the install command in the uninstall input field) and for the detection rule use the detection script added in the repo.
best,
Oliver
Hi,
This is absolutely great, a complete game changer for us!
Thank you!
We are looking to allow use of characters in the PIN.
How would I go about changing this so it would allow it?
When I try to now it only allows numbers.
e.g. if i was to set my pin to Shower01 for instance.
What would need to be changed in the scripts?
Kind regards
Ah actually there is a small bug the added Test-IncrementNumber I added later is preventing the fact of EnhancedPIN check which is the allowance of characters…. So, I’m going to fix this so that it is working again.
Have you ever got around to fixing this? Thanks.
I took the time today and verified it once more in my lab and it is working as expected. I don’t have any issues with EnhancedPIN (allowing chars). So, my assumption about the decrement function is not correct. I can use the popup with numbers only and also with chars. Where do you experience still a problem?
Sry for the late reply. So Enhanced PIN is enabled by default correct? and I just need to change the pop box verbiage from Numbers to char?
No EnhancedPIN is not enabled by default, you have to set the registry key, as soon as it is set, the Form ist recognizes it and will handle chars correctly. Did you try to set the EnhancedPIN already? HKLM\SOFTWARE\Policies\Microsoft\FVE\UseEnhancedPin
If “HKLM\SOFTWARE\Policies\Microsoft\FVE\UseEnhancedPin” is not set by the Powershell/intune then no. I used the script without any modification. Any recommendation how should I go about setting it up?
You can simply set the registry key via a PS script in Intune and deploy it to the devices, it is not available in the device configuration profiles in Intune.
Thank you I will try it and update you with my result.
Hi, this is a great solution to accomplish the PIN at start-up.
Is there a way to prevent closing the Enter Pin dialog box before input has been put in?
That would be possible by changing the Cancel button code to add something like this if ($textboxNewPin.Text.Length -eq 0) { return } and registering a new event function which captures Form event Closing and a similar check and if ($textboxNewPin.Text.Length -eq 0) { e.Cancel = true; } but this time set event arg Cancel to true. registering would be something like this $formBitLockerStartupPIN.add_FormClosing($Form_FormClosing)
best,
Oliver
Thank for the reply.
Going to test this.
Hi @oliver
I’m having issues when deploying this as the app appears to install but nothing prompts, perhaps im wrapping the files incorrectly if you have seen this before?
Thanks
Hi Jim,
typically, if you added all files (especially ServiceUI.exe) and then used command powershell -ex bypass -file SetBitLockerPin.ps1 for install and the DetectBitLockerPin.ps1 as the detection script it should run without issues. No special config etc. is necessary.
best,
Oliver
Hi Oliver,
This is pretty awesome! Wondering if you noticed when users want to change their PIN, if say they can’t re-call their current PIN. There’s the “Reset a Forgotten PIN” option but it appears to require Admin permissions to be able to change their PIN without requiring their current one. We currently are migration from MBAM to Intune for Bitlocker and with the MBAM client, it adds an app in Control Panel called “Bitlocker Encryption Options” that actually lets standard users change the PIN without administrative permissions. It appears there’s no policy or setting in Intune that I’ve found to allow standard users to reset a forgotten PIN. Wondering would something you created above for setting a PIN be utilized for resetting forgotten PINs as well? I’ve seen multiple users run into this issue and without a reasonable solution.
Hey Moe,
technically you could modify the script in a way to accomplish your goal. First, we would need to take care of the detection logic. We are not able to run an Intune package again when it is installed. Intune will check the detection logic and tell you it is already installed. So, if we find a way to re-run the Intune package, we can modify the script to simply delete the pin protector and re-create a pin protector which is technically a pin reset. This could be achieved by calling a remove of the current pin protector (one liner, Remove-BitLockerKeyProtector, but be careful it must be in a try catch to prevent error if there is no pin protector set) and the existing add of the pin protector (Add-BitLockerKeyProtector). To let the package run again we would need to modify something on the device which results in a failed detection logic evaluation, which then results in a package running again and this package would then remove an existing pin protector and add a new one, which is a pin reset. The current detection logic is querying the protector state. You could modify it to query a file for example in the filesystem. If the file does not exist, detection logic will be false the Intune will allow you to re-run the package. Now we would need something convenient to delete the file easily to re-run the Intune PIN package. The file should be in a user writeable location to allow standard users to delete the file and then finally let the PIN package re-run. I don’t have a great idea right now how to make this convenient. Maybe a small helper presenting the user a dialog with a reset pin button, which is deleting the file and then calling companyportal:ApplicationId= to call the company portal PIN package. it will not start right away; user has to click there once more but maybe that’s a workaround?
best,
Oliver
Hi Oliver, great tool. I’m implementing this solution and have found if the calling script SetBitLockerPin.ps1 is terminated, the Popup.ps1 script still continues to run. This got me to thinking of adding the creation of the protector within Popup.ps1 (this also would mean there is no need to pass the PIN between the two processes). Is there any reason or issue I’m not aware of that lead you to choose the route to pass the PIN back to the calling SetBitLockerPIN.ps1 script?
Hi Marc,
Yes, there is a reason. The Protector must be set in system context and the popup must run in user context. You will not be able to add the protector from popup in user context. That why I did the architecture like this to solve this issue to have a popup and in addition an execution of a process in system context.
best,
Oliver
The bitlocker policy has worked great but the application is erroring during enrolment.
Has anyone else experienced this?
Hi,
it is not meant to be targeted as required install during ESP/Autopilot enrollment. As it will try to show a popup and user can’t interact with it.
best,
Oliver
I use a requirement script to detect if it is still in autopilot proces. If not the Win32 Package is kicking directly in when autopilot process is finished.
Requirement Script:
$UserEnabled=Get-LocalUser defaultuser0 -ErrorAction SilentlyContinue | Select Enabled -ExpandProperty Enabled
if(-not($UserEnabled -eq “True”)) {
Write-Output 1
#Write-Host “Non AutoPilot Session Confirmed”
Exit 0
}
This solution was posted here before.
Hi Oliver,
the input in the Ui is based on a QWERTY keyboard. Since we operate mainly from Germany we would like to change this to QWERTZ. Is there any way to do this ?
Thanks a lot !
Regards,
Alex
Hi,
I played around a bit and changed values for textboxNewPin.UseSystemPasswordChar = True to Fale to see the input. I have a German keyboard configured in my Windows 11 device and for example the letter z is typed correctly by typing z. If it would switch to en-US QWERTY it would type Y but it does not on my system. So, the input control adapts to what is configured in windows and honors this setting on my system. That’s exactly the behavior I know from the .NET controls. Do you have a special language configuration in regards to UI, Formats etc on your devices?
best,
Oliver
Hey,
Somehow, a user managed to set a StartUp Pin with just 6 digits. Now we wanted to change that to a new Pin with 8 digits via Change Bitlocker Pin Dialogue.
But: It’s not possible, because the dialogue wants to have at least 8 digits for the old Pin.
Could you tell me, where I have to dig to remove that requirement to have 8 digits when changing that Pin?
Thanks a lot!
Hi everything works! Only the language seems not to when started from Intune (still in English) instead if I run the script from powershell I can see the Gui in Italian I translate in the json file
Any idea?
Are you sure that the updated .json file is in the .intunewin package? I don’t see any problem if it is working on your device, it should work the same way when correctly put into the .intunewin.
best,
Oliver
Yes I’m sure…..I also extracted the .intunewin package and checked
Hmm… okay then the only way to find why it’s failing on your side would be to create debug output for the part
$uiLang = $(Get-Culture).Name
$language = Get-Content language.json -Encoding UTF8 | ConvertFrom-Json
There it must fail and something is not recognized. write the uiLang and language into a file and deploy ist and see what is written there.
best,
Oliver
When the app is running on the machines, it pops up for the user to create the pin, the user inputs the PIN as requested and the bitlocker is enabled to use that PIN but then the app states as failed to install in the toast notifications. The PIN is still applied but the prompt keeps appearing as Intune detects it as having failed installing. Any ideas?
Something with the Detection method must go wrong. Did you verify the Detection logic script by executing it manually? What does it say?
Hi All,
We experienced an issue during Autopilot when we used a requirement PS-script to detect if Autopilot process is active. We assigned it to all devices and used this requirement PS-Script:
$UserEnabled=Get-LocalUser defaultuser0 -ErrorAction SilentlyContinue | Select Enabled -ExpandProperty Enabled
if(-not($UserEnabled -eq “True”)) {
Write-Output 1
Exit 0
}
Issue with this is that during Account Setup the local profile is no longer enabled, so the BitLocker PIN UI is behind the Autopilot screen and takes a lot of time and in the end it will fail. I update the requirement PS-script with this:
$Status=Get-Process -Name cloudexperiencehostbroker -ErrorAction SilentlyContinue
if(-not($Status.Responding -eq ‘True’)) {
Write-Output 1
Exit 0
}
This process is still running when Autopilot is finished but after a reboot the process is not running anymore, and the Set BitLocker PIN app is executed. To get the device compliant (BItLocker) the device requires a reboot anyway.
Hope this helps
Regards
Tom Klaver (InSpark)
Hi Oliver,
Though I ran through most part of the steps to get App created and uploaded on to Intune, but out of my 2 machines it is showing “Waiting for install status” on one in Intune Portal’s Managed App status page and no errors are being displayed until now. What could be the possible cause and solution to this?
Regards,
Paras
How did you assign the app? Available or required, and was it shown and the PIN was set and finally you are just missing the final status in Intune, or did you never get the app in the required scenario? So, how was the exact assignment and intent?
Hi, is it simple to change the PIN requirement from 8 to 6?
That’s a simple policy change in Intune. The dialog will recognize that and prompt you for 6 then.
https://learn.microsoft.com/en-us/mem/intune/protect/endpoint-security-disk-encryption-profile-settings#bitlocker—os-drive-settings
Great – I was thinking the text would have to be amended. Thanks!
Hi,
I have just found this blog and it looks like a great solution.
I’m currently testing with a Windows 11 VM, I have tried assigning the app as required to a device group and also Available to ‘All users,’ the app deploys to the VM and I see the input boxes but shortly after entering the pin I get the notification ‘installation failed.’
Any suggestions?
I have created the .intunewin that contains DetectBitLockerPin.ps1, Popup.ps1, ServiceUI.exe, SetBitLockerPin.ps1, language.json
I have set the Detection rules to use a custom detection script (DetectBitLockerPin.ps1)
The BitLocker settings for the OS Drive are Compatible TPM startup PIN = Allowed
Hi AJ,
did you enable the TPM support on the Win11 VM? And you could try to verify your setup by using psexec.exe from sysinternals and running the SetBitLockerPin.ps1 from a “system context” PowerShell to see what happens.
best,
Oliver
Hello, when a user closes the prompt it flags up as a failed install but doesn’t reattempt another install?
This is with the detection script.
The reattempt should occur after max. 60 min. when the client checks in again and evaluates the apps and detection rules again. Did you wait that long?
Hi Oliver – we are using this with some success but are experiencing an issue when resetting the device using Intune that it retains the old PIN in TPM. Is this expected?
Hi Stuart,
Yes, that is normal behavior. A reset will not reset a TPM PIN.
best,
Oliver
Hi Oliver,
Thanks for your script unfortunatly it did not work as it was failing due to detection script used “Write-Output $(Get-BitLockerVolume -MountPoint $env:SystemDrive).KeyProtector | Where { $_.KeyProtectorType -eq ‘TpmPin’ }”
I have used this script for Surface pro 8
Error “The application was not detected after installation completed successfully (0x87D1041C)”
Windows version :Windows 10.0.19044.2251
Is there any alternative scripts to be used instead.
Hey Thyagu,
if you run the detection script what is the output. If the BitLocker script is working and setting the TpmPin protector it should not fail. So, I think something might have gone wrong with the set of the PIN and therefore the detection script failed. So please execute the script and have a look at the output.
best,
Oliver
Thank you so much for this. It helped me a lot!
But theres on thing:
If you just cancel or close the little popup it will sometimes (8 out of 10 times for me) set the TpmPin flag even though theres was no input by the user.
just try it on a vm, run the script and close the pop up.
@Oliver: my knowledge for PowerShell is very slim and I wouldn’t know how to fix that.
Would love if you could fix this. Thanks so much in advance!
I tried to reproduce and it didn’t set anything. Did you make any changes on your own?
Where and How to use the below command. Could you please explain
.\IntuneWinAppUtil -c .\SetBitLockerPin -s SetBitLockerPin.ps1 -o .\ -q
Hi this is the command to wrap the whole folder into the .intunewin which can be distributed later.
Hi Oliver
Is there a reason why the Popup.ps1 and SetBitlockerPin.ps1 is two different scripts? As far as i understand the running context of these two are the same, and dumping files on the disk for grabs later seems over-complicating. Maybe i’m missing something 🙂
Also would there be a way to implement a rotation of PIN after a specific amount of days?
Thanks
Hi Morten,
the scripts are not running in the same context. The popup script is called from the user context via ServiceUI.exe. That’s why we need different scripts here. The popup script asks for the PIN, dumps it on the disk and the other script takes it as input in the system context to set it finally.
For a rotation, you would need to implement a few changes. You would need to store the script somewhere C:\ProgramData for example permanently and then register a scheduled task to call it after x-days and ask for the new PIN. In addition, you would like to check more precisely if the rotated PIN was actually set. So, nothing you would do in 5 min. work.
best,
Oliver