
Microsoft made it finally happen and provides an integrated way to deploy Win32 Apps via the Intune Management Extension. This is by far the biggest step forward in the Modern Management field. Until now the community came up with lots of ways to utilize PowerShell scripts to finally install some Win32 Apps. By doing this you need to take care of the content location, availability, distribution, the app install, and verification logic. All this is now available in the enhanced Intune Management Extension. As a short refresh regarding Intune Management Extension, I recommend to read my blog articles about it, where you find a lot of information regarding the architecture, the inner workings, and troubleshooting advises:
Part 1 Deep dive Microsoft Intune Management Extension – PowerShell Scripts
Part 2 Deep dive Microsoft Intune Management Extension – PowerShell Scripts
Both articles are very relevant to this new feature as they all describe the architecture and technical details regarding the Intune Management Extension itself. Exactly this Intune Management Extension is used now for deploying Win32 apps packaged as .intunewin file format. It’s even better, the new functionality can be used to basically transport everything in a package and trigger a certain command line for execution. This is not a end to end walk-through how to use the feature in regards of the Intune portal or on the client itself. For this check out other great articles found in my last section End to end usage walk-throughs?. This is an article all about the inner workings of this new capability, a deep dive into the new technology itself.
Table of content for easy navigation
- How do we get packaged apps now?
- How can we decode Intune Win32 app packages?
- Why is the .intunewin packaged like this?
- Where can I find details of the Win32 App deployment?
- Intune Management Extension Agent working folders?
- Agent execution context when processing .intunewin files?
- What are the retry and execution intervals?
- Current Limitations (as per date Oct-2018)?
- End to end usage walk-throughs?
- Further recommended reading (deep dives, ideas, etc)?
How do we get packaged apps now?
To get a Win32 apps deployed via the Intune Management Extension we first need to package the content we want to distribute. Microsoft decided to use the same approach like they did for the macOS world, where they provide a small tool to create the packages – Microsoft Intune App Wrapping Tool for macOS. A similar tool to create these packages is available for the Windows world now. This tool is called:
Microsoft Win32 Content Prep Tool
For all of you with ConfigMgr experience, the new feature to deploy Win32 apps with Intune can be compared a little bit with the Packages and Programs functionality within ConfigMgr, but with some additions.
The usage of the Microsoft Intune Win32 App Packaging Tool (IntuneWinAppUtil.exe) is quite simple. We specify a folder and the executable and create then an yourappname.intunewin file. This is our packaged app which we then can upload to the Intune service. The command line of the tool is this:
IntuneWinAppUtil -c -s -o <-q>
To dig a little deeper we inspect the resulting package in detail now. After successful execution it will generate the .intunewin file from the specified source folder and setup file. For MSI setup files, this tool will retrieve required information for later usage in the Intune portal. To explore this a little bit I captured the output and highlighted some important facts there, to gain understanding how the tool is working.

As seen the tool is executed with the necessary parameters to create a package for Google Chrome Enterprise Edition Browser, which is provided as a .msi file. A sub folder called Chrome is in the same folder as the IntuneWinAppUtil. The command line then is:
IntuneWinAppUtil.exe -c .\Chrome -s GoogleChromeStandaloneEnterprise64.msi -o .\ -q
If we look at the green highlighted output now we find some very important information appearing which is exactly describing the workflow:
- Compressing the source folder and its files to a sub folder ‘content’ with the new extension .intunewin
- Encrypting the compressed file
- Computing SHA256 hash
- Generating a detection.xml file in a sub folder ‘metadata’
- Compressing complete working folder and create again an .intunewin file
As we can see a normal zip compression is used and therefore it is easy to verify all this by opening the generated package with our favorite archive application:

We can see the content folder and metadata folder. Where the content folder stores the encrypted .intunewin file:

and the metadata folder contains the detection.xml file:

If we now have a look at the detection.xml file we can see the information gathered about the package and msi file:
<ApplicationInfo xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" ToolVersion="1.0.0.0">
<Name>Google Chrome</Name>
<UnencryptedContentSize>52284458</UnencryptedContentSize>
<FileName>GoogleChromeStandaloneEnterprise64.intunewin</FileName>
<SetupFile>GoogleChromeStandaloneEnterprise64.msi</SetupFile>
<EncryptionInfo>
<EncryptionKey>Rj9EtHeHGYMv5HYBpyobrmp0rVg0pzIy0TwO9PnSRg8=</EncryptionKey>
<MacKey>5kxZeuk6xfeMak+r/9hzbwS0vBUW1jBMhgN10Jy7XBQ=</MacKey>
<InitializationVector>2AK05qM3tm/5ijDnlFPISA==</InitializationVector>
<Mac>zI8vragiGb1VtbVRiKo3lPkJldZGZB4juX50MCNrmDw=</Mac>
<ProfileIdentifier>ProfileVersion1</ProfileIdentifier>
<FileDigest>Nzl3O6e70W1P0kJDJiWh3eU6gCVOhODNNy7mspfplQA=</FileDigest>
<FileDigestAlgorithm>SHA256</FileDigestAlgorithm>
</EncryptionInfo>
<MsiInfo>
<MsiProductCode>{A4BC9C54-4589-3A4C-8217-9FA00262F471}</MsiProductCode>
<MsiProductVersion>67.92.84</MsiProductVersion>
<MsiUpgradeCode>{C1DFDF69-5945-32F2-A35E-EE94C99C7CF4}</MsiUpgradeCode>
<MsiExecutionContext>System</MsiExecutionContext>
<MsiRequiresLogon>false</MsiRequiresLogon>
<MsiRequiresReboot>false</MsiRequiresReboot>
<MsiIsMachineInstall>true</MsiIsMachineInstall>
<MsiIsUserInstall>false</MsiIsUserInstall>
<MsiIncludesServices>false</MsiIncludesServices>
<MsiIncludesODBCDataSource>false</MsiIncludesODBCDataSource>
<MsiContainsSystemRegistryKeys>true</MsiContainsSystemRegistryKeys>
<MsiContainsSystemFolders>false</MsiContainsSystemFolders>
</MsiInfo>
</ApplicationInfo>
A detailed review shows us the file and encryption information and in addition the MSI file information. This information is used by the Intune portal to pre-populate some Intune app definitions for us.
The MSI information is only available when a msi file is packaged. If we package a setup.exe for example you will not see the entire section in the detection.xml file.
How can we decode Intune Win32 app packages?
I wrote a small utility to convert a .intunewin package back to it’s original sources. You can read more about it on my separate blog post here: How to decode Intune Win32 App Packages
Why is the .intunewin packaged like this?
This is pretty simple to explain. The portal and the Intune service gets all necessary information to deal with the app (in this case Google Chrome). The msi information listed in the detection.xml is used to simplify the setup within the Intune UI by pre-filling the app form during creation. For example by adding the install and uninstall commands for the msi automatically:
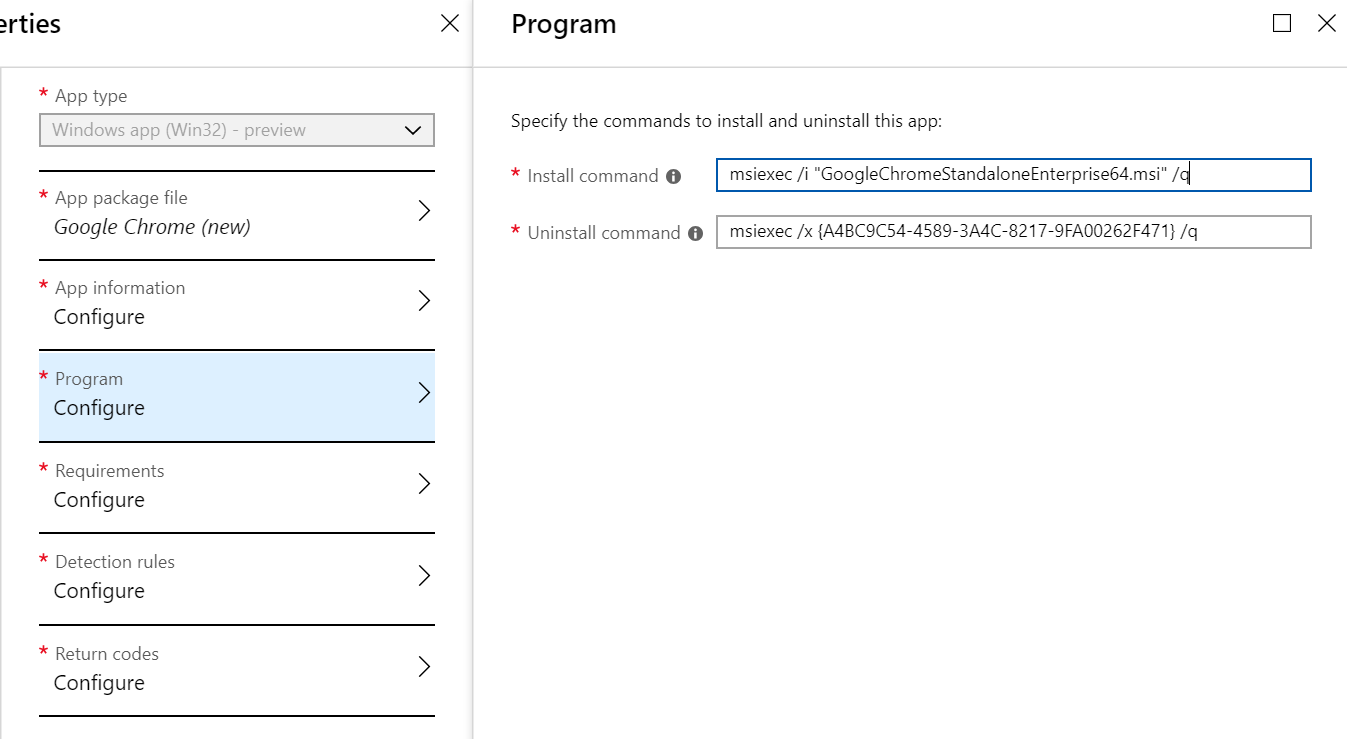
The EncryptionInfo is used to store it with your Intune tenant to gain access to the uploaded .intunewin package. The encrtypted .intunewin (located in the content folder) can be distributed safely to the Intune back-end services responsible for content distribution without getting exposed to others, only the tenant who uploaded the file has the EncryptionInfo and can decrypt the file.
Where can I find details of the Win32 App deployment?
The Intune Management Extension tracks some details of the Win32 apps in the registry at: HKLM\SOFTWARE\Microsoft\IntuneManagementExtension\Apps\

The yellow highlighted names provide us the execution commands for install and uninstall and the attempts and results of it.
If we look at the green highlighted GUID at HKLM\SOFTWARE\Microsoft\IntuneManagementExtension\Win32Apps\73d664e4-0886-4a… we can see it matches my Azure AD user object ID. To compare it I got the details via Azure AD PowerShell:

The red highlighted GUID (b0f62b79-e464-4f95-afe2-ed99eb612fe5) is the application GUID which is assigned by the Intune service back-end. This can be easily traced by looking at the graph data with the Graph Explorer from Microsoft:
https://developer.microsoft.com/en-us/graph/graph-explorer
In my example I used this to retrieve the details of my uploaded app:
https://graph.microsoft.com/beta/deviceAppManagement/mobileApps/b0f62b79-e464-4f95-afe2-ed99eb612fe5
This is the detailed information about the uploaded Win32 .intunewin app:
{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#deviceAppManagement/mobileApps/$entity",
"@odata.type": "#microsoft.graph.win32LobApp",
"id": "b0f62b79-e464-4f95-afe2-ed99eb612fe5",
"displayName": "Google Chrome (new)",
"description": "Google Browser",
"publisher": "Google",
"largeIcon": null,
"createdDateTime": "2018-09-21T09:38:11.4343585Z",
"lastModifiedDateTime": "2018-09-21T09:39:16.2037636Z",
"isFeatured": true,
"privacyInformationUrl": null,
"informationUrl": null,
"owner": "",
"developer": "",
"notes": "",
"uploadState": 1,
"publishingState": "published",
"committedContentVersion": "1",
"fileName": null,
"size": 52284512,
"installCommandLine": "msiexec /i \"GoogleChromeStandaloneEnterprise64.msi\" /q",
"uninstallCommandLine": "msiexec /x {A4BC9C54-4589-3A4C-8217-9FA00262F471} /q",
"applicableArchitectures": "x64",
"minimumFreeDiskSpaceInMB": null,
"minimumMemoryInMB": null,
"minimumNumberOfProcessors": null,
"minimumCpuSpeedInMHz": null,
"msiInformation": null,
"setupFilePath": null,
"minimumSupportedOperatingSystem": {
"v8_0": false,
"v8_1": false,
"v10_0": false,
"v10_1607": true,
"v10_1703": false,
"v10_1709": false,
"v10_1803": false
},
"detectionRules": [
{
"@odata.type": "#microsoft.graph.win32LobAppProductCodeDetection",
"productCode": "{A4BC9C54-4589-3A4C-8217-9FA00262F471}",
"productVersionOperator": "notConfigured",
"productVersion": null
}
],
"installExperience": {
"runAsAccount": "system"
},
"returnCodes": [
{
"returnCode": 0,
"type": "success"
},
{
"returnCode": 1707,
"type": "success"
},
{
"returnCode": 3010,
"type": "softReboot"
},
{
"returnCode": 1641,
"type": "hardReboot"
},
{
"returnCode": 1618,
"type": "retry"
}
]
}
Intune Management Extension Agent working folders?
If we have a look at the file system at:
C:\Program Files (x86)\Microsoft Intune Management Extension\Content C:\Windows\IMECache
we can find some interesting folders where the agent is downloading the content and detection scripts and stores the actual MSI log files:

To allow proper installation and execution of LOB Win32 apps, anti-malware settings (ASR rules and Defender AV) should exclude the following directories from being scanned (compare here).
X64 client
C:\Program Files (x86)\Microsoft Intune Management Extension\Content C:\Windows\IMECache
X86 client
C:\Program Files\Microsoft Intune Management Extension\Content C:\Windows\IMECache
Agent execution context when processing .intunewin files?
The agent is bound to the same restrictions during execution like we know them for PowerShell scripts, meaning the calling process (the Intune Management Extension agent) is a 32-bit process. This can result in some unexpected behavior. For example when trying to package a simple .ps1 file within a .intunewin and trying to execute cmdlets in this scripts which are only available in a 64-bit environment. We then have to use a technique to restart the PowerShell script as a 64-bit process. This is described in my previous articles and I have built a Intune PowerShell script template to simplify the start for this, which can be found on my GitHub here https://github.com/okieselbach/Intune/blob/master/ManagementExtension-Samples/IntunePSTemplate.ps1. This can also affect installers packaged as .intunewin when they assume a 64-bit environment!
For PowerShell execution Intune added a UI element to control 64-bit execution, but this is not available for Win32 apps and therefore the re-start technique must still be used here.
If no restart technique is used keep in mind that environment variables must be handled with care from 32-bit processes. For example if you like to target the %windir%\System32 environment from a 32-bit process you have to use %windir%\Sysnative otherwise you will land in %windir%\SysWOW64. Visit the linkt to read more about the file system redirector: https://docs.microsoft.com/en-us/windows/desktop/winprog64/file-system-redirector
What are the retry and execution intervals?
The agent has default values for retry and execution:
- max. of 3 retries
- interval between the retries is 5 min.
- max. execution run time is 60 min.
these limits are not adjustable at the moment.
Current Limitations (as per date Oct-2018)?
No user context app installation(added 29th of Oct 2018)No system context installation without user logged on(added 29th of Oct 2018)- No dependency support
- No supersedence
No support for Delivery Optimization(added 26th of Nov 2018)- No integration into Enrollment Status Page, no wait for Win32 app installs
No toast notification suppression(added 21th of Jan 2019)- No ordered installations, sequencing like .NET Framework install before App X
- Current application size is capped at
2GB8GB per app (changed 29th of Oct 2018)
End to end usage walk-throughs?
Good walk-throughs on how to use the feature with the Intune portal and the end user experience can be found here:
Deploy Win32 Applications with Microsoft Intune
http://www.scconfigmgr.com/2018/09/24/deploy-win32-applications-with-microsoft-intune/
Deploy customized Win32 apps via Microsoft Intune
https://www.petervanderwoude.nl/post/deploy-customized-win32-apps-via-microsoft-intune/
Intune – sidecar for Win32 apps revealed
http://gerryhampsoncm.blogspot.com/2018/09/intune-sidecar-for-win32-apps-revealed.html
Intune Win32 App deployment – A gamechanger
https://ccmexec.com/2018/10/intune-win32-app-deployment-a-gamechanger/
Official documentation can be seen here
Intune Standalone – Win32 app management
https://docs.microsoft.com/en-us/intune/apps-win32-app-management
Further recommended reading (deep dives, ideas, etc)?
Intune Win32 app requirements deep dive
https://tech.nicolonsky.ch/intune-win32-app-requirements-deep-dive/
Remember to check back frequently as Intune progresses and the feature will be enhanced in short cycles. I will update the article accordingly.
Happy packaging, deploying and troubleshooting Win32 apps with Intune!
Nice write up once again.
The current limitations are not earth shocking or real blocking for deployments.
PS. Maybe add screenshot what user will see/get notificationd when deploy is in progress?
I have an application i need to install via a .bat file. in the past i compiled this set of files and its batch into an exe using iexpress and the cmd.exe /c batchfile.bat. Would I still perform this operation and then convert this into an .intunewin file?
Thanks
Lee
Hi Lee,
You can skip the iexpress part and just compile all your files into .intunewin and provide the command line in Intune. That‘s it, should work easily.
Best,
Oliver
Hi Oliver. I got some issues with an app deployed this way. It fails during unzipping due to long file path. Intune gives following error: Error unzipping downloaded content. (0x87D30067)
<![LOG[Exception occurs when unzipping Win32App user session 1, the Exception is System.IO.PathTooLongException: Sökvägen eller filnamnet, eller båda två, innehåller för många tecken. Det fullständiga filnamnet måste innehålla färre än 260 tecken och katalognamnet färre än 248.
How can I resolve this issue?
Hi Gurstav,
I think I would try to do a workaround. I would install the app via a custom install wrapper script. I would package the program files of my app into a 7zip or regular zip archive and my custom installer would then extract to e.g. C:\temp to avoid long path names and would call the win32 installer/setup from there, wait for exit and gather exit code to return the exit code to the Intune Win32 package.
best,
Oliver
Oliver/Gustav,
i also have the 0x87D30067 message on a new win32.intune package and this is the only page according to google related to that error icw Intune.
Checked the folder depth with cmd /s in powershell to check -gt 170, not 1 file. So it must be under the 170chars.
The folder (c:\progfilesx86\intunemgt etc\staged\app_id) is about 56 chars.
So, imho its not above 248 or 260 :D.
I will try to wrap it and deploy with PS. And check this page the coming weeks for any updates.
A small update;
After some check I see that my PS folder depth check was not showing the correct info. After checking it myself i have found the folder with the issues, it is only 2 MB data. Also tried to use TARGETDIR as msiexec paramater, but it keeps extracting the folder to the Staging folder.
Did you manage to sort this out? I have the same issue. This is with Adobe Acrobat DC
Hi, I think I would try to do a workaround. I would install the app via a custom install wrapper script. I would package the program files of my app into a 7zip or regular zip archive and my custom installer would then extract to e.g. C:\temp to avoid long path names and would call the win32 installer/setup from there, wait for exit and gather exit code to return the exit code to the Intune Win32 package.
best,
Oliver
Using the Win32 App Packinging tool to create an intunewin file from an exe, I open the detection.xml file but I am not seeing the product code to use to the uninstall command. In the xml file I have encryption key, mac key, initialization vector, mac, profileidentifier, file digest and file digest algorithm. Which one of those do I use in the uninstall command when uploading the intunewin to Intune?
Thanks
Hi dj56,
you don’t need to look up the MSI product code by your own. When you package a .msi file as .intunewin the tool will generate the MSI information in the detection.xml. The portal will pick this information and automatically fill out the form for you with the relevant information for install command and uninstall command. If there is no msi information in the detection.xml it’s either you didn’t package a .msi file, maybe you packaged a setup.exe for example. Only with .msi files the Packaging Tool will provide this additional information as a .msi file is a standardized way of packaging which can be read programmatically. Other installers are all different and therefor no programmatic reading is possible. A setup.exe can be a Nullsoft installer, InstallShield or whatever… a ton of possibilities. Only .msi are read for product code to make your life a bit easier when uploading.
best,
Oliver
So FireFox for example or any software that only provides an exe to download, is using this tool the best way to create the intunewin file to upload into Intune?
Oliver,
Can we use parameters in the command line in Intune? Lets say setup.exe -config.xml ?
Hi LJ,
Of course when you use the Win32 app support you can package whatever you want and then specify any command line for install and uninstall. So your example is absolutely possible, yes!
Best,
Oliver
Hi,
nice Infos, like always. Im wondering, how to uninstall a Programm from Company Portal?? We only have “reinstall”… If we uninstall the normal way, then the Software has still the status “installed” in Company Portal.
Under Intune Troubleshoot –> my device –> Managed Apps (Preview) Chrome has Installation Status failed (The application was not detected after installation completed successfully)
😀 Not very Usefull at the Moment…
But wait 🙂 it says “The application was not detected after installation completed successfully”, then your detection rule is not correct. Have a look at the detection rule.
Hi Martin,
thanks :-). The installed status will change after some time to installed failed. You need to wait a bit longer. This is because the detection rule of the intunewin will run and find your app not installed anymore and will get this status and reports it. This status will then be reflected in the company portal. If your app is not targeted as an available deployment, a required deployment, then the agent will reinstall the app again. For company portal you have the available deployment and therefore it will only be reported as failed as it is not there anymore, your detection rule failed. You could hit reinstall as a user and the app gets installed again. If you like to uninstall the app you might target a dedicated uninstall assignment.
best,
Oliver
Hi Oliver,
yes i know about the uninstall per assignment, but i think if you have not only required but also optional software, the end user needs the possibilty to uninstall. Maybe this will be on the Roadmap.
Thanks
Martin
Hi Oliver – really useful info as always – many thanks for this blog!
I’m struggling with trying to uninstall a user context Win32 application where I need to use an environment variable from the user context to generate the path to the uninstall executable.
Example I’m using is ‘Postman’ which installs in user context ok using ‘Postman-win64-6.7.4-Setup.exe -s’.
To uninstall I’ve tried using ‘%LOCALAPPDATA%\Postman\Update.exe –uninstall -s’ which fails, but works if I expand %LOCALAPPDATA% to the full path – although this is not a workaround as only works for a single user.
I tried changing the uninstall command to ‘cmd.exe /c “%LOCALAPPDATA%\Postman\Update.exe –uninstall -s”‘ and the Intune log then showed the problem – the above expands to:
IntuneManagementExtension.log
cmd.exe /c “C:\Windows\system32\config\systemprofile\AppData\Local\Postman\Update.exe –uninstall -s”
The log sequence indicates the variable expansion is done before the user context is loaded.
I’ve also tried putting the variable expansion into a .bat file, including the install package and then calling that, but I get:
IntuneManagementExtension.log
cmd.exe /c Uninstall.bat
…
[Win32App] Launch Win32AppInstaller in user session
[Win32App] lastWin32Error 5 after CreateProcess
Uninstall.bat is:
@echo OFF
%LOCALAPPDATA%\Postman\Update.exe –uninstall -s
EXIT /B %ERRORLEVEL%
Any ideas or solutions would be much appreciated!
Hi Mark,
I tried to reproduce your issue but actually I found another issue with the latest agent. I wasn’t able to run the installer in user context as the installer now uses C:\Windows\IMECache and there are missing permissions on the folder for the logged on user to access the folder. Therefore my install command could not run and access the installer files. I’m in contact with the PG to clarify this. As soon as I have more info I’ll keep you updated and try to look at your initial issue.
best,
Oliver
Hi Oliver,
I have the same problem (missing permissions on IMECache), so I am also interested in the solution from PG. Thank you!
Kind regards,
Jef
Hi,
in the meantime I’ve spoken to the PG and they reprod and confirmed the behaviro and it will be fixed. An updated agent will be published soon, be patient :-).
best,
Oliver
I confirmed the new agent is published, version 1.16.113.0. It fixes the problem but may have still a timing issue during user context detection rule execution, which will be addressed in Intune 1903 release, which is broadly available in April normally.
best,
Oliver
Thank you Oliver, for the information!
Kind regards,
Jef
Hay, Oliver! i switched the “Client apps” workload over to Intune, but the “intune management extension” was only installed on non-co-managed devices. Such as pure-intune managed devices. Any advise?
– Bendik G
Hey Bendik,
so normally the agent gets pushed as soon as you assign a PS Script or Win32 app to an user/device. Did you check the Eventlog, MDM Diagnostics, and Registry for the EnterpriseDesktopAppCSP, and the SystemProfile path for a MSI log file. Basically all the locations I mention in my 3 part series blog posts? Co-Management is support according to the MS docs, so maybe there is a kind of install failure, any traces of install attempts would be good as a starting point.
best,
Oliver
Hello Oliver,
So i found a workaround, by deploying the Intune Mangement Extension, using SCCM. But now I have a different problem; I have tried deploying applications from Intune using required installation. I have tried with both Microsoft store applications, that are synced to Intune and win32 applications such as 7-zip. In both cases, when logging in to one of my windows 10 devices, i can see the Intune Management Extension working, and is attempting to install the applications deployed from Intune. But after a while, the installation fails, with the error code “0x87D300C9”.
best,
Bendik G
I am having trouble while trying to import intunewin file. Created a program in Azure portal and after providing my requirements and detection method and when click on Ok application created but while trying to upload the file after 65% got An unexpected error occurred during upload xxxxx.intunewin file. [ ] Try adding this app again. May I know what may be the reason the size of the application is around 1.75 GB.
Hi Raj,
Sorry for the delayed response. Hm I’m not sure what causes this I would probably do the following things. Try to clean the browser cache, maybe it is something related to the browser. then make sure you are using the latest packaging tool for intunewin (https://github.com/Microsoft/Intune-Win32-App-Packaging-Tool). My largest app I’ve used with Intune so far was around 1 GB in size and it was working. Which browser are you using, I’m using most of the time Chrome, maybe this is also a factor. Otherwise you might raise a support ticket.
best,
Oliver
I have MS VIsio and Project in Intune, both are above 2GB. I think you cannot click OK after selecting the .INTUNE file when the file is too big. I once had an issue with uploading files, downloading the newest version of the package tool fixed that.
This 3 part article is fantastic. Thanks a lot really valuable!
I have a question about app updates: Say I deploy an app through an MSI (business line app) f.e. MyAppv1.msi. After some time I want to update this app because I noticed an error. Would it suffice to change the MSI file with a new MyAppv1.msi or do I have to take other steps to show it’s an updated version. My question is actually how does intune know the app should be updated? If I change the title of the app I assume it wouldn’t be considered an update?
Is the only way to work with detection rules?
Thank you!
My question doesn’t make a lot of sense as I’ve just noticed that only Win32 apps allow for detection rules. But still wondering how updates work for both MSI and Win32 apps.
Hi Stoebel,
just upload the new package and a new version is reflected in the Company Portal and installed for the user which has the old version installed. Mor on this here https://docs.microsoft.com/en-us/intune/apps-add#installing-updating-or-removing-required-apps
Installing, updating, or removing required apps
Intune will automatically reinstall, update, or remove a required app within 24 hours, rather than waiting for the 7 day re-evaluation cycle.
Intune will automatically reinstall, update, or remove a required app based on the following conditions:
If an end user uninstalls an app that you have required to be installed on the end user’s device, Intune will automatically reinstall the app when this schedule elapses.
If a required app install fails or somehow the app is not present on the device, Intune evaluates compliance and reinstalls the app when this schedule elapses.
An admin targets an app as available to a user group and an end user installs the app from the company portal on the device. Later, the admin updates the app from v1 to v2. Intune will update the app when this schedule elapses, provided that any previous version of the app is still present on the device.
If the admin deploys uninstall intent and the app is present on the device and failed to uninstall, Intune evaluates compliance and uninstalls the app when this schedule elapses.
best,
Oliver
Note sure if my question came through. If it did you can delete this reply.
Hi Oliver. I am facing a hurdle when trying to install a printer driver with pnputil, where it claims it cannot find pnputil. If I run the script locally it installs just fine, if I run it through a “printer installation” deployed through “company portal” when I debug it shows that pnputil cannot be found. So something in the way company portal / intuneextension runs it is causing it to not find pnputil. Can you assist?
Hey Lenny,
this might be due to the 32-bit execution of the script. pnputil is only available as a 64-bit binary on a 64-bit Windows device. So try to use my wrapper here https://github.com/okieselbach/Intune/blob/master/ManagementExtension-Samples/IntunePSTemplate.ps1 to restart the script in 64-bit and then the script will find pnputil. When you test your script on Windows it will run in 64-bit and that’s why you see it working during testing.
best,
Oliver
Hallo Oliver,
First of all, your posts are super helpful, thanks for that.
But now let’s try to figure out how to manage the local cache for win32apps.
Problem:
Win32apps, that are not MSIs, only self-programmed exes / scripts or something else cannot be uninstalled via “Add Remove Programs”, as the source files are deleted immediately after the installation. This situation poses considerable problems for support.
How / where can we manage the settings for the local cache “C: \ Windows \ IMECache”?
Hi Andreas,
You simply can’t. And even MSI’s when triggered via Add Remove Programs can’t be repaired as the installing MSI was in IMECache and is not available for the repair, you will see a dialog searching for the msi in IMECache. The way to uninstall currently is to explicitly target an uninstall to that particular device. MS is aware of this, larger customers reported this to them es well. Currently it is unknown if they are planning to mitigate it and if so when. I’m sorry I can’t deliver better news here.
best,
Oliver
Oliver, is there a reason we need a script to restart itself as a 64-bit process and we can’t just point our “install command” to the 64-bit powershell executable?